Check Point 156-215.80 Check Point Certified Security Administrator R80 Online Training
Check Point 156-215.80 Online Training
The questions for 156-215.80 were last updated at Apr 10,2025.
- Exam Code: 156-215.80
- Exam Name: Check Point Certified Security Administrator R80
- Certification Provider: Check Point
- Latest update: Apr 10,2025
With the User Directory Software Blade, you can create R80 user definitions on a(an) ___________ Server.
- A . NT domain
- B . SMTP
- C . LDAP
- D . SecurID
Which of the following is NOT a component of a Distinguished Name?
- A . Organizational Unit
- B . Country
- C . Common Name
- D . User container
What are the three authentication methods for SIC?
- A . Passwords, Users, and standards-based SSL for the creation of secure channels
- B . Certificates, standards-based SSL for the creation of secure channels, and 3DES or AES128 for encryption
- C . Packet Filtering, certificates, and 3DES or AES128 for encryption
- D . Certificates, Passwords, and Tokens
You have enabled “Extended Log” as a tracking option to a security rule.
However, you are still not seeing any data type information.
What is the MOST likely reason?
- A . Logging has disk space issues. Change logging storage options on the logging server or Security Management Server properties and install database.
- B . Content Awareness is not enabled.
- C . Identity Awareness is not enabled.
- D . Log Trimming is enabled.
What is the order of NAT priorities?
- A . Static NAT, IP pool NAT, hide NAT
- B . IP pool NAT, static NAT, hide NAT
- C . Static NAT, automatic NAT, hide NAT
- D . Static NAT, hide NAT, IP pool NAT
What is the order of NAT priorities?
- A . Static NAT, IP pool NAT, hide NAT
- B . IP pool NAT, static NAT, hide NAT
- C . Static NAT, automatic NAT, hide NAT
- D . Static NAT, hide NAT, IP pool NAT
What is the order of NAT priorities?
- A . Static NAT, IP pool NAT, hide NAT
- B . IP pool NAT, static NAT, hide NAT
- C . Static NAT, automatic NAT, hide NAT
- D . Static NAT, hide NAT, IP pool NAT
What is the order of NAT priorities?
- A . Static NAT, IP pool NAT, hide NAT
- B . IP pool NAT, static NAT, hide NAT
- C . Static NAT, automatic NAT, hide NAT
- D . Static NAT, hide NAT, IP pool NAT
Which of the following is an identity acquisition method that allows a Security Gateway to identify Active Directory users and computers?
- A . UserCheck
- B . Active Directory Query
- C . Account Unit Query
- D . User Directory Query
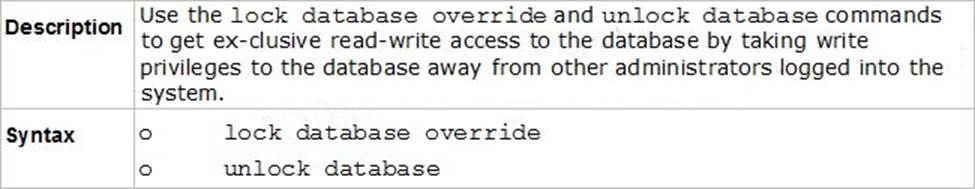
Ken wants to obtain a configuration lock from other administrator on R80 Security Management Server Operating System. He can do this via WebUI or via CLI.
Which command should he use in CLI?
- A . remove database lock
- B . The database feature has one command: lock database override.
- C . override database lock
- D . The database feature has two commands: lock database overrideand unlock database. Both will work.
Latest 156-215.80 Dumps Valid Version with 528 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund