Check Point 156-215.80 Check Point Certified Security Administrator R80 Online Training
Check Point 156-215.80 Online Training
The questions for 156-215.80 were last updated at Apr 25,2025.
- Exam Code: 156-215.80
- Exam Name: Check Point Certified Security Administrator R80
- Certification Provider: Check Point
- Latest update: Apr 25,2025
VPN gateways authenticate using ___________ and ___________ .
- A . Passwords; tokens
- B . Certificates; pre-shared secrets
- C . Certificates; passwords
- D . Tokens; pre-shared secrets
In R80 spoofing is defined as a method of:
- A . Disguising an illegal IP address behind an authorized IP address through Port Address Translation.
- B . Hiding your firewall from unauthorized users.
- C . Detecting people using false or wrong authentication logins
- D . Making packets appear as if they come from an authorized IP address.
The __________ is used to obtain identification and security information about network users.
- A . User Directory
- B . User server
- C . UserCheck
- D . User index
Which Check Point feature enables application scanning and the detection?
- A . Application Dictionary
- B . AppWiki
- C . Application Library
- D . CPApp
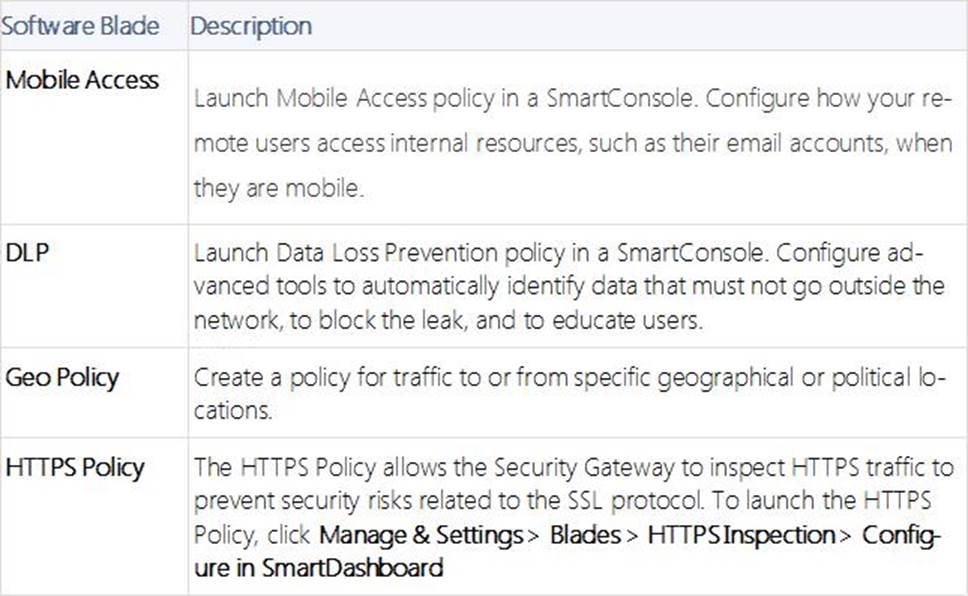
DLP and Geo Policy are examples of what type of Policy?
- A . Standard Policies
- B . Shared Policies
- C . Inspection Policies
- D . Unified Policies
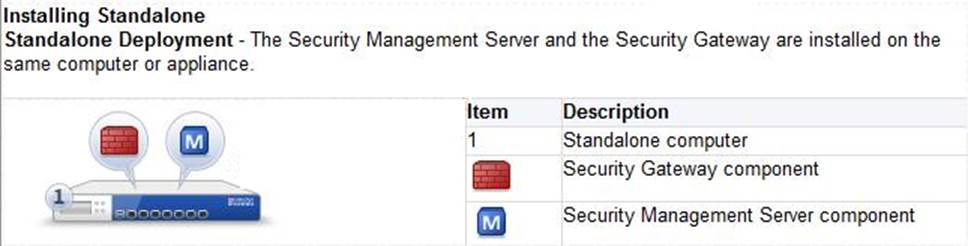
In which deployment is the security management server and Security Gateway installed on the same appliance?
- A . Bridge Mode
- B . Remote
- C . Standalone
- D . Distributed
A _________ VPN deployment is used to provide remote users with secure access to internal corporate resources by authenticating the user through an internet browser.
- A . Clientless remote access
- B . Clientless direct access
- C . Client-based remote access
- D . Direct access
Which of the following statements is TRUE about R80 management plug-ins?
- A . The plug-in is a package installed on the Security Gateway.
- B . Installing a management plug-in requires a Snapshot, just like any upgrade process.
- C . A management plug-in interacts with a Security Management Server to provide new features and support for new products.
- D . Using a plug-in offers full central management only if special licensing is applied to specific features of the plug-in.
Gaia can be configured using the _______ or ______ .
- A . GaiaUI; command line interface
- B . WebUI; Gaia Interface
- C . Command line interface; WebUI
- D . Gaia Interface; GaiaUI
Gaia can be configured using the _______ or ______ .
- A . GaiaUI; command line interface
- B . WebUI; Gaia Interface
- C . Command line interface; WebUI
- D . Gaia Interface; GaiaUI
Latest 156-215.80 Dumps Valid Version with 528 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund