Assuming that name is a String obtained by an <apex:inpucText> tag on a Visualforce page, which two SOQL queries performed are safe from SOQL injection? Choose 2 answers
Assuming that name is a String obtained by an <apex:inpucText> tag on a Visualforce page, which two SOQL queries performed are safe from SOQL injection? Choose 2 answers
A)

B)
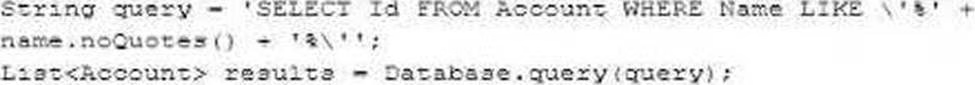
C)
![]()
D)

A . Option A
B . Option B
C . Option C
D . Option D
Answer: A, C
Explanation:
Option A:
String query = ‘SELECT Id FROM Account WHERE Name LIKE ‘%’ + String.escapeSingleQuotes(name) + ‘%”;
List<Account> results = Database.query(query);
This option uses String.escapeSingleQuotes(name) to sanitize the name variable. This method escapes any single quotes in the input, preventing malicious input from breaking out of the string context in the SOQL query.
Reference: Salesforce Apex Developer Guide – Escaping Single Quotes
Why Safe: By escaping single quotes, it mitigates the risk of SOQL injection attacks that rely on manipulating string literals.
Option C:
String query = ‘%’ + name + ‘%’;
List<Account> results = [SELECT Id FROM Account WHERE Name LIKE :name];
This option uses a bind variable (:name) in the SOQL query. When variables are bound in this way, Salesforce automatically handles escaping and ensures that the input cannot alter the structure of the query.
Reference: Salesforce Apex Developer Guide – Using Apex Variables in SOQL and SOSL Queries Why Safe: Bind variables are the recommended way to include user input in SOQL queries safely, as they prevent injection by treating the input as a parameter rather than part of the query string.
Option B:
String query = ‘SELECT Id FROM Account WHERE Name LIKE ‘%’ + name.noQuotes() + ‘%”; List<Account> results = Database.query(query);
The method noQuotes() does not exist in the Apex String class. Therefore, this code does not properly sanitize the name variable.
Reference: Salesforce Apex Developer Guide – String Class Methods
Why Unsafe: Without proper sanitization, the name variable could contain malicious SOQL code, leading to injection vulnerabilities.
Option D:
String query = ‘SELECT Id FROM Account WHERE Name LIKE ‘%’ + name + ‘%”; List<Account> results = Database.query(query);
This option directly concatenates the name variable into the query string without any form of sanitization or escaping.
Reference: Salesforce Apex Developer Guide – SOQL Injection Overview
Why Unsafe: Direct concatenation of user input without sanitization leaves the application
vulnerable to SOQL injection attacks.
Conclusion:
Safe Options: A and C are safe from SOQL injection because they properly handle user input through escaping and bind variables, respectively.
Unsafe Options: B and D are unsafe as they do not adequately prevent SOQL injection.
Latest DEX-450 Dumps Valid Version with 456 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

