Which of the following methods can achieve this requirement?
A company is generating confidential data that is saved on their on-premises data center. As a backup solution, the company wants to upload their data to an Amazon S3 bucket. In compliance with its internal security mandate, the encryption of the data must be done before sending it to Amazon S3. The company must spend time managing and rotating the encryption keys as well as controlling who can access those keys.
Which of the following methods can achieve this requirement? (Select TWO.)
A . Set up Client-Side Encryption using a client-side master key.
B . Set up Server-Side Encryption with keys stored in a separate S3 bucket.
C . Set up Client-Side Encryption with Amazon S3 managed encryption keys.
D . Set up Server-Side Encryption (SSE) with EC2 key pair.
E . Set up Client-Side Encryption with a customer master key stored in AWS Key Management Service
(AWS KMS).
Answer: A,E
Explanation:
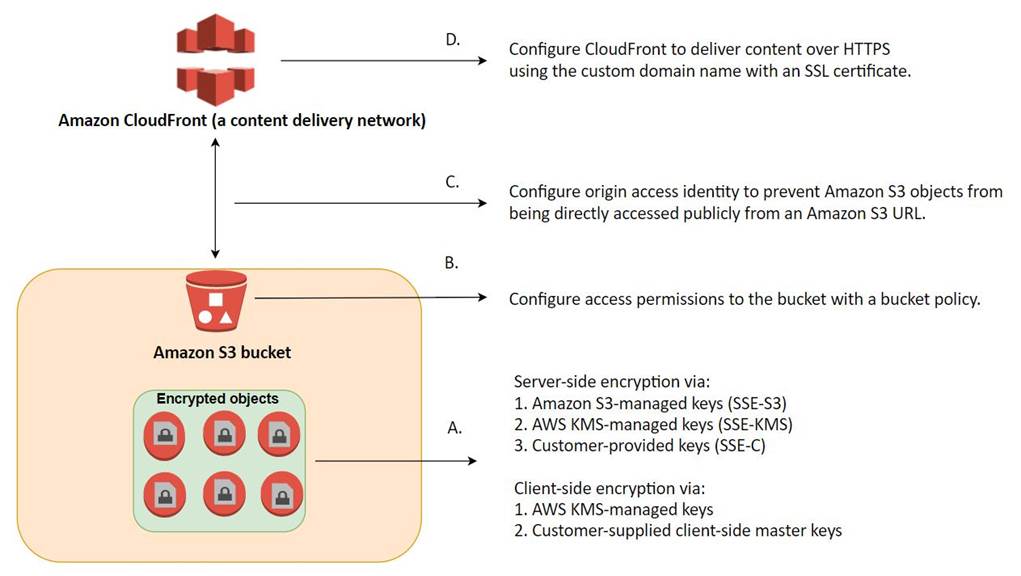
Data protection refers to protecting data while in-transit (as it travels to and from Amazon S3) and at rest (while it is stored on disks in Amazon S3 data centers). You can protect data in transit by using SSL or by using client-side encryption. You have the following options for protecting data at rest in Amazon S3: Use Server-Side Encryption C You request Amazon S3 to encrypt your object before saving it on disks in its data centers and decrypt it when you download the objects.
Use Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3)
Use Server-Side Encryption with AWS KMS-Managed Keys (SSE-KMS)
Use Server-Side Encryption with Customer-Provided Keys (SSE-C)
Use Client-Side Encryption C You can encrypt data client-side and upload the encrypted data to Amazon
S3. In this case, you manage the encryption process, the encryption keys, and related tools. Use Client-Side Encryption with AWS KMSCManaged Customer Master Key (CMK) Use Client-Side Encryption Using a Client-Side Master Key
Hence, the correct answers are:
– Set up Client-Side Encryption with a customer master key stored in AWS Key Management Service (AWS KMS).
– Set up Client-Side Encryption using a client-side master key.
The option that says: Set up Server-Side Encryption with keys stored in a separate S3 bucket is incorrect because you have to use AWS KMS to store your encryption keys or alternatively, choose an AWS-managed CMK instead to properly implement Server-Side Encryption in Amazon S3. In addition, storing any type of encryption key in Amazon S3 is actually a security risk and is not recommended.
The option that says: Set up Client-Side encryption with Amazon S3 managed encryption keys is incorrect because you can’t have an Amazon S3 managed encryption key for client-side encryption. As its name implies, an Amazon S3 managed key is fully managed by AWS and also rotates the key automatically without any manual intervention. For this scenario, you have to set up a customer master key (CMK) in AWS KMS that you can manage, rotate, and audit or alternatively, use a client-side master key that you manually maintain.
The option that says: Set up Server-Side encryption (SSE) with EC2 key pair is incorrect because you can’t use a key pair of your Amazon EC2 instance for encrypting your S3 bucket. You have to use a client-side master key or a customer master key stored in AWS KMS. References:
http://docs.aws.amazon.com/AmazonS3/latest/dev/UsingEncryption.html
https://docs.aws.amazon.com/AmazonS3/latest/dev/UsingClientSideEncryption.html
Check out this Amazon S3 Cheat Sheet:
https://tutorialsdojo.com/amazon-s3/
Latest SAA-C03 Dumps Valid Version with 400 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

