What is the best way to achieve this?
A Solutions Architect needs to set up a bastion host in Amazon VPC. It should only be accessed from the corporate data center via SSH .
What is the best way to achieve this?
A . Create a large EC2 instance with a security group which only allows access on port 22 via the IP address of the corporate data center. Use a private key (.pem) file to connect to the bastion host.
B . Create a large EC2 instance with a security group which only allows access on port 22 using your own pre-configured password.
C . Create a small EC2 instance with a security group which only allows access on port 22 using your own pre-configured password.
D . Create a small EC2 instance with a security group which only allows access on port 22 via the IP
address of the corporate data center. Use a private key (.pem) file to connect to the bastion host.
Answer: D
Explanation:
The best way to implement a bastion host is to create a small EC2 instance which should only have a security group from a particular IP address for maximum security. This will block any SSH Brute Force attacks on your bastion host. It is also recommended to use a small instance rather than a large one because this host will only act as a jump server to connect to other instances in your VPC and nothing else.
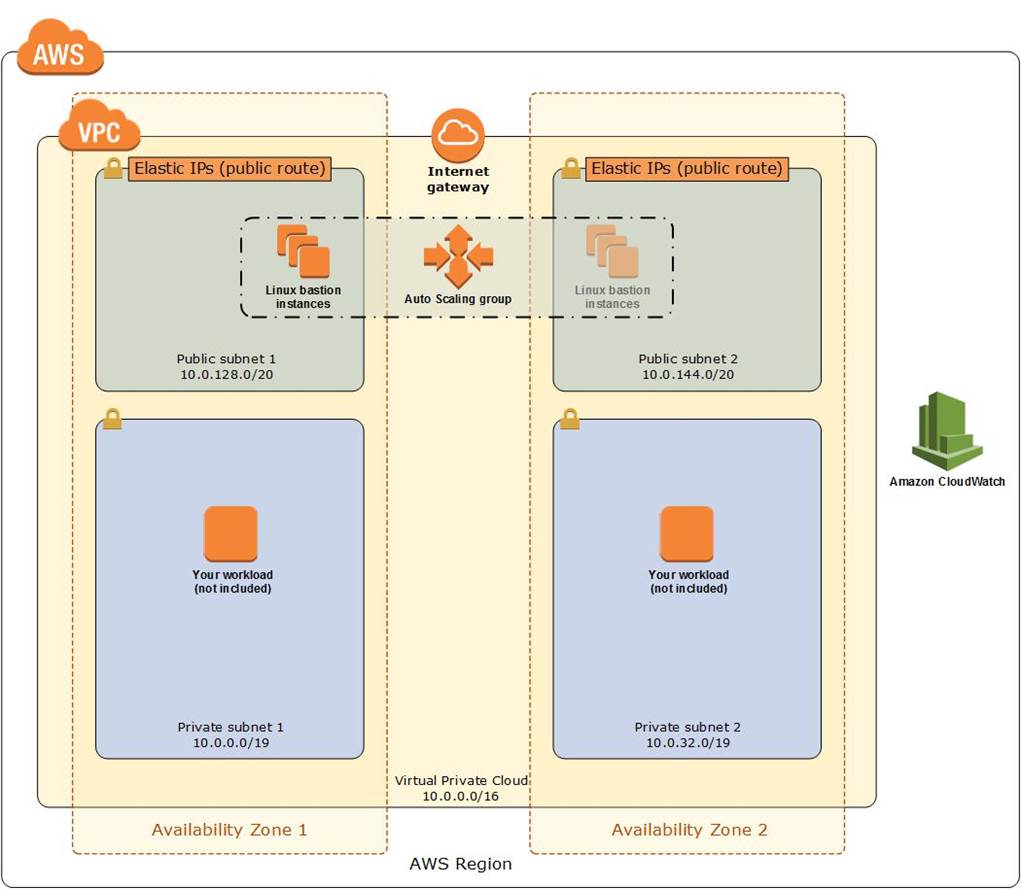
Therefore, there is no point of allocating a large instance simply because it doesn’t need that much computing power to process SSH (port 22) or RDP (port 3389) connections. It is possible to use SSH with an ordinary user ID and a pre-configured password as credentials but it is more secure to use public key pairs for SSH authentication for better security.
Hence, the right answer for this scenario is the option that says: Create a small EC2 instance with a security group which only allows access on port 22 via the IP address of the corporate data center. Use a private key (.pem) file to connect to the bastion host.
Creating a large EC2 instance with a security group which only allows access on port 22 using your own pre-configured password and creating a small EC2 instance with a security group which only allows access on port 22 using your own pre-configured password are incorrect. Even though you have your own pre-configured password, the SSH connection can still be accessed by anyone over the Internet, which poses as a security vulnerability.
The option that says: Create a large EC2 instance with a security group which only allows access on port
22 via the IP address of the corporate data center. Use a private key (.pem) file to connect to the bastion
host is incorrect because you don’t need a large instance for a bastion host as it does not require much
CPU resources.
References:
https://docs.aws.amazon.com/quickstart/latest/linux-bastion/architecture.html
https://aws.amazon.com/blogs/security/how-to-record-ssh-sessions-established-through-a-bastion-host/
Check out this Amazon VPC Cheat Sheet:
https://tutorialsdojo.com/amazon-vpc/
Latest SAA-C03 Dumps Valid Version with 400 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

