Which configuration should be used to ensure that the access to the resources is secured and not compromised?
A Solutions Architect is building a cloud infrastructure where EC2 instances require access to various AWS services such as S3 and Redshift. The Architect will also need to provide access to system
administrators so they can deploy and test their changes.
Which configuration should be used to ensure that the access to the resources is secured and not compromised? (Select TWO.)
A . Store the AWS Access Keys in the EC2 instance.
B . Assign an IAM role to the Amazon EC2 instance.
C . Store the AWS Access Keys in AC
E . Enable Multi-Factor Authentication.
F . Assign an IAM user for each Amazon EC2 Instance.
Answer: B,D
Explanation:
In this scenario, the correct answers are:
– Enable Multi-Factor Authentication
– Assign an IAM role to the Amazon EC2 instance
Always remember that you should associate IAM roles to EC2 instances and not an IAM user, for the purpose of accessing other AWS services. IAM roles are designed so that your applications can securely make API requests from your instances, without requiring you to manage the security credentials that the applications use. Instead of creating and distributing your AWS credentials, you can delegate permission to make API requests using IAM roles.
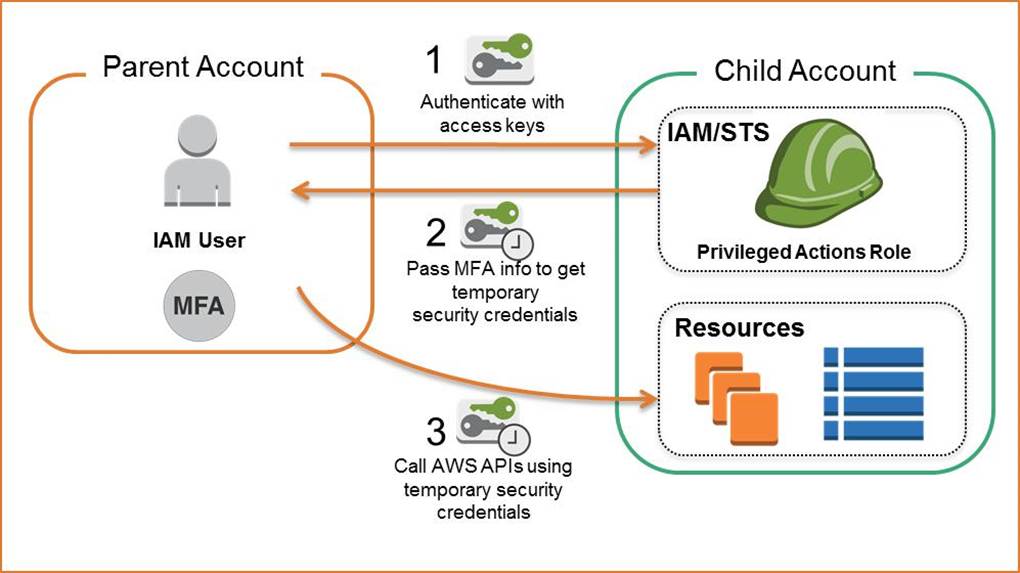
AWS Multi-Factor Authentication (MFA) is a simple best practice that adds an extra layer of protection on top of your user name and password. With MFA enabled, when a user signs in to an AWS website, they will be prompted for their user name and password (the first factor―what they know), as well as for an authentication code from their AWS MFA device (the second factor―what they have). Taken together, these multiple factors provide increased security for your AWS account settings and resources. You can enable MFA for your AWS account and for individual IAM users you have created under your account. MFA can also be used to control access to AWS service APIs.
Storing the AWS Access Keys in the EC2 instance is incorrect. This is not recommended by AWS as it can be compromised. Instead of storing access keys on an EC2 instance for use by applications that run on the instance and make AWS API requests, you can use an IAM role to provide temporary access keys for these applications.
Assigning an IAM user for each Amazon EC2 Instance is incorrect because there is no need to create an IAM user for this scenario since IAM roles already provide greater flexibility and easier management. Storing the AWS Access Keys in ACM is incorrect because ACM is just a service that lets you easily provision, manage, and deploy public and private SSL/TLS certificates for use with AWS services and your internal connected resources. It is not used as a secure storage for your access keys. References:
https://aws.amazon.com/iam/details/mfa/
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/iam-roles-for-amazon-ec2.html
Check out this AWS IAM Cheat Sheet:
https://tutorialsdojo.com/aws-identity-and-access-management-iam/
Latest SAA-C03 Dumps Valid Version with 400 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

