Fortinet NSE6_FWB-6.1 Fortinet NSE 6 – FortiWeb 6.1 Online Training
Fortinet NSE6_FWB-6.1 Online Training
The questions for NSE6_FWB-6.1 were last updated at Feb 07,2026.
- Exam Code: NSE6_FWB-6.1
- Exam Name: Fortinet NSE 6 - FortiWeb 6.1
- Certification Provider: Fortinet
- Latest update: Feb 07,2026
What role does FortiWeb play in ensuring PCI DSS compliance?
- A . It provides the ability to securely process cash transactions.
- B . It provides the required SQL server protection.
- C . It provides the WAF required by PCI.
- D . It provides credit card processing capabilities.
C
Explanation:
FortiWeb protects against attacks that lead to sensitive data exposure such as SQL Injection and other injection types. Additionally, FortiWeb inspects all web server outgoing traffic for sensitive data such as Social Security numbers, credit card numbers and other predefined or custom based sensitive data.
Reference: https://www.gordion.de/fileadmin/user_upload/SG-PCI-Compliance.pdf
What can an administrator do if a client has been incorrectly period blocked?
- A . Nothing, it is not possible to override a period block.
- B . Manually release the ID address from the temporary blacklist.
- C . Force a new IP address to the client.
- D . Disconnect the client from the network.
B
Explanation:
Block Period
Enter the number of seconds that you want to block the requests. The valid range is 1C3,600 seconds. The default value is 60 seconds.
This option only takes effect when you choose Period Block in Action.
Note: That’s a temporary blacklist so you can manually release them from the blacklist.
Reference: https://docs.fortinet.com/document/fortiweb/6.3.1/administration-guide/600188/configuring-bot-detection-profiles
Review the following configuration:
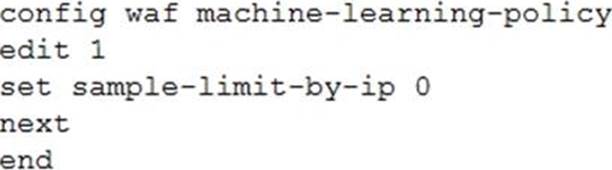
What is the expected result of this configuration setting?
- A . When machine learning (ML) is in its collecting phase, FortiWeb will accept an unlimited number of samples from the same source IP address.
- B . When machine learning (ML) is in its running phase, FortiWeb will accept an unlimited number of samples from the same source IP address.
- C . When machine learning (ML) is in its collecting phase, FortiWeb will not accept any samples from any source IP addresses.
- D . When machine learning (ML) is in its running phase, FortiWeb will accept a set number of samples from the same source IP address.
How does FortiWeb protect against defacement attacks?
- A . It keeps a complete backup of all files and the database.
- B . It keeps hashes of files and periodically compares them to the server.
- C . It keeps full copies of all files and directories.
- D . It keeps a live duplicate of the database.
B
Explanation:
The anti-defacement feature examines a web site’s files for changes at specified time intervals. If it detects a change that could indicate a defacement attack,
the FortiWeb appliance can notify you and quickly react by automatically restoring the web site contents to the previous backup.
Reference: https://help.fortinet.com/fweb/551/Content/FortiWeb/fortiweb-admin/anti_defacement.htm
What is one of the key benefits of the FortiGuard IP reputation feature?
- A . It maintains a list of private IP addresses.
- B . It provides a document of IP addresses that are suspect, so that administrators can
manually update their blacklists. - C . It is updated once per year.
- D . It maintains a list of public IPs with a bad reputation for participating in attacks.
D
Explanation:
FortiGuard IP Reputation service assigns a poor reputation, including virus-infected clients and malicious spiders/crawlers.
Reference: https://docs.fortinet.com/document/fortiweb/6.1.1/administration-guide/137271/blacklisting-whitelisting-clients
Refer to the exhibit.
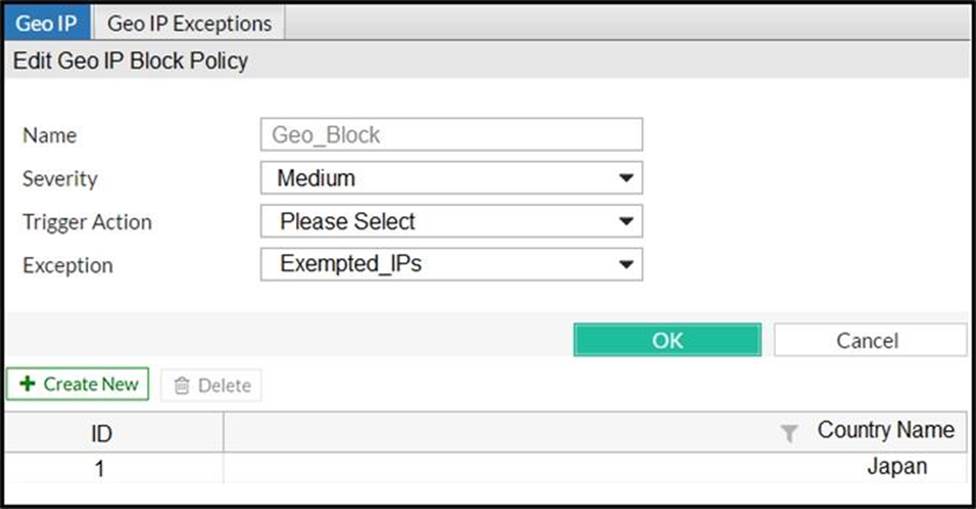
FortiWeb is configured to block traffic from Japan to your web application server. However, in the logs, the administrator is seeing traffic allowed from one particular IP address which is geo-located in Japan.
What can the administrator do to solve this problem? (Choose two.)
- A . Manually update the geo-location IP addresses for Japan.
- B . If the IP address is configured as a geo reputation exception, remove it.
- C . Configure the IP address as a blacklisted IP address.
- D . If the IP address is configured as an IP reputation exception, remove it.
CB
Explanation:
IP reputation leverages many techniques for accurate, early, and frequently updated identification of compromised and malicious clients so you can block attackers before they target your servers.
IP blacklisting is a method used to filter out illegitimate or malicious IP addresses from accessing your networks. Blacklists are lists containing ranges of or individual IP addresses that you want to block.
Reference:
https://docs.fortinet.com/document/fortiweb/6.3.5/administration-guide/137271/blacklisting-whitelisting-clients
https://www.imperva.com/learn/application-security/ip-blacklist/
Which statement about local user accounts is true?
- A . They are best suited for large environments with many users.
- B . They cannot be used for site publishing.
- C . They must be assigned, regardless of any other authentication.
- D . They can be used for SSO.
B
Explanation:
You can configure the Remedy Single Sign-On server to authenticate TrueSight Capacity Optimization users as local users.
Reference: https://docs.bmc.com/docs/TSCapacity/110/setting-up-local-user-authentication-in-remedy-sso-743238341.html
Which algorithm is used to build mathematical models for bot detection?
- A . HCM
- B . SVN
- C . SVM
- D . HMM
C
Explanation:
FortiWeb uses SVM (Support Vector Machine) algorithm to build up the bot detection model
Reference: https://docs.fortinet.com/document/fortiweb/6.3.7/administration-guide/193258/machine-learning
When is it possible to use a self-signed certificate, rather than one purchased from a commercial certificate authority?
- A . If you are a small business or home office
- B . If you are an enterprise whose employees use only mobile devices
- C . If you are an enterprise whose resources do not need security
- D . If you are an enterprise whose computers all trust your active directory or other CA server
D
Explanation:
This can include SSL/TLS certificates, code signing certificates, and S/MIME certificates. The reason why they’re considered different from traditional certificate-authority signed certificates is that they’re created, issued, and signed by the company or developer who is responsible for the website or software being signed. This is why self-signed certificates are considered unsafe for public-facing websites and applications.
Reference: https://sectigostore.com/page/what-is-a-self-signed-certificate/
True transparent proxy mode is best suited for use in which type of environment?
- A . New networks where infrastructure is not yet defined
- B . Flexible environments where you can easily change the IP addressing scheme
- C . Small office to home office environments
- D . Environments where you cannot change the IP addressing scheme
B
Explanation:
Does not require changes to the IP address scheme of the network. Requests are destined for a web server and not the FortiWeb appliance. This operation mode supports the same feature set as True Transparent Proxy mode.
Reference: https://docs.fortinet.com/document/fortiweb/6.3.0/administration-guide/211763/planning-the-network-topology
Latest NSE6_FWB-6.1 Dumps Valid Version with 30 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

