VMware 1V0-81.20 Associate VMware Security Online Training
VMware 1V0-81.20 Online Training
The questions for 1V0-81.20 were last updated at Feb 08,2026.
- Exam Code: 1V0-81.20
- Exam Name: Associate VMware Security
- Certification Provider: VMware
- Latest update: Feb 08,2026
When using VMware Carbon Black Live Response, what command will show all active processes?
- A . dir
- B . list
- C . ls
- D . ps
Which three are key features of VMware Carbon Black Cloud Enterprise EDR? (Choose three.)
- A . self-service security remediation
- B . continuous and centralized recording
- C . attack chain visualization and search
- D . live response for remote remediation
- E . frequent Antivirus pattern updates
In Workspace ONE UEM, from which menu would you access Workspace ONE Intelligence?
- A . Apps & Books
- B . General Settings
- C . Device
- D . Monitor
Which option would be considered an example of aHardware Based Exploit?
- A . SQL Injection
- B . Social Engineering
- C . Jail Breaking
- D . Denial of Service
Which three default connectors are available in Workspace ONE Intelligence to execute automation actions? (Choose three.)
- A . ServiceNow
- B . vRealize Operations Manager
- C . Slack
- D . Log Insight
- E . Workspace ONE UEM
If the Compromised Protection switch is enabled in Workspace ONE UEM, what is the
expected behavior on compromised devices in the environment?
- A . A tag is assigned to the compromised devices and the admin gets notification
- B . Compromised devices are automatically Enterprise Wiped
- C . A block is set for all network connections except to the VMware servers
- D . Devices are marked as non-compliant and the admin gets a notification
Refer to the exhibit.
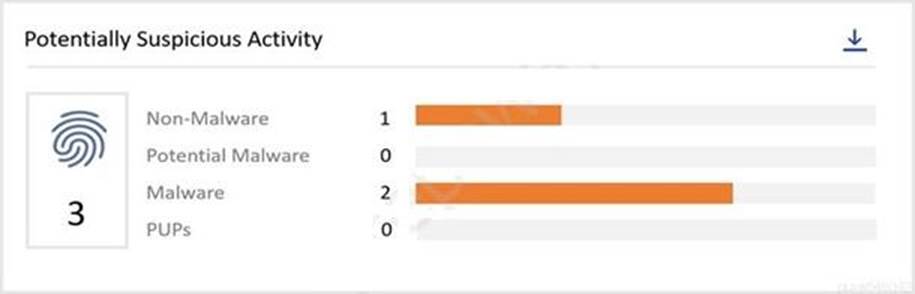
From theVMware Carbon Black Cloud console, what page do you go to after clicking the Non-Malware bar in the Potentially Suspicious Activity chart?
- A . Notifications page with the selected alert filtered
- B . Reputations page with the selected reputation filtered
- C . Investigate page with the selected reputation filtered
- D . Alerts page with the selected alert filtered
Which three Workspace ONE UEM capabilities are used to configure security policies on Windows 10 desktops? (Choose three.)
- A . Application Profiles
- B . Custom XML
- C . Custom Attributes
- D . Baselines
- E . Native Profiles
What is the default user’s network range when creating a new access policy rule in Workspace ONE Access?
- A . 10.0.0.0/8
- B . ALL RANGES
- C . 192.168.0.0/16
- D . LOCAL SUBNET
Which three common mitigations for social engineering attacks? (Choose three.)
- A . user training
- B . filtering Email attachments
- C . update Antivirus software
- D . remove applications
- E . blocking execution of suspicious files
Latest 1V0-81.20 Dumps Valid Version with 55 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

