Which type of compromise is occurring?
Refer to the exhibit.
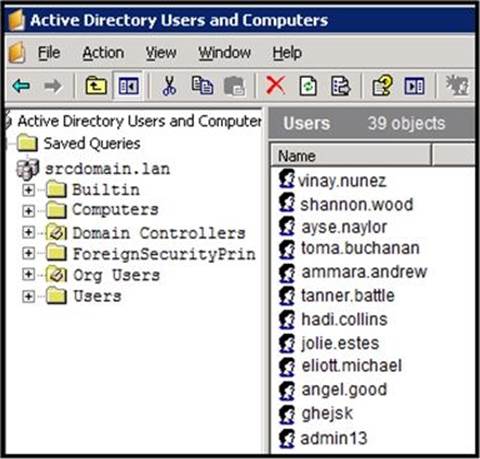
An engineer is investigating a case with suspicious usernames within the active directory. After the engineer investigates and cross-correlates events from other sources, it appears that the 2 users are privileged, and their creation date matches suspicious network traffic that was initiated from the internal network 2 days prior .
Which type of compromise is occurring?
A . compromised insider
B . compromised root access
C . compromised database tables
D . compromised network
Answer: D
Latest 350-201 Dumps Valid Version with 139 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

