What should you use?
HOTSPOT
You have a Microsoft 365 tenant.
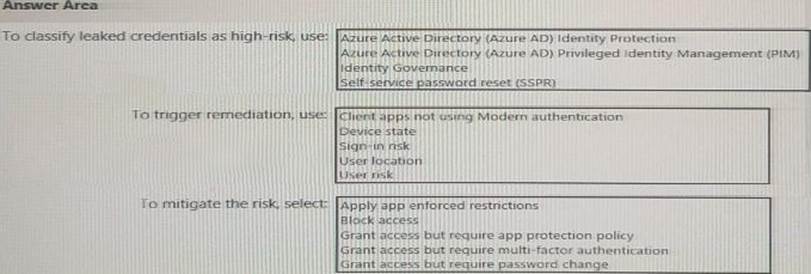
You need to identify users who have leaked credentials.
The solution must meet the following requirements.
• Identity sign-Ins by users who ate suspected of having leaked credentials.
• Rag the sign-ins as a high risk event.
• Immediately enforce a control to mitigate the risk, while still allowing the user to access applications.
What should you use? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Answer: 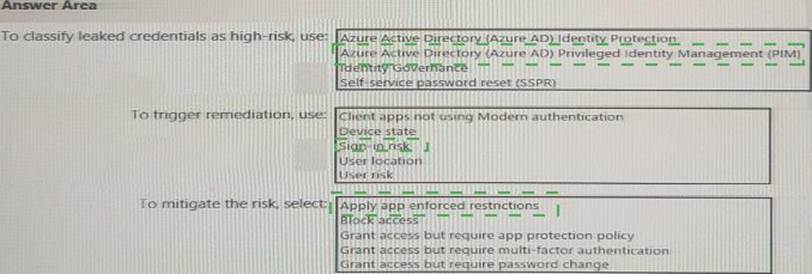
Latest SC-300 Dumps Valid Version with 106 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund
Subscribe
Login
0 Comments
Inline Feedbacks
View all comments

