Microsoft AZ-202 Microsoft Azure Developer Certification Transition Online Training
Microsoft AZ-202 Online Training
The questions for AZ-202 were last updated at Feb 08,2026.
- Exam Code: AZ-202
- Exam Name: Microsoft Azure Developer Certification Transition
- Certification Provider: Microsoft
- Latest update: Feb 08,2026
Topic 1, Litware Inc.Overwiew
Background
You are a developer for Litware Inc., a SaaS company that provides a solution for managing employee expenses. The solution consists of an ASP.NET Core Web API project that is deployed as an Azure Web App.
Overall architecture
Employees upload receipts for the system to process. When processing is complete, the employee receives a summary report email that details the processing results. Employees then use a web application to manage their receipts and perform any additional tasks needed for reimbursement
Receipt processing
Employees may upload receipts in two ways:
– Uploading using an Azure Files mounted folder
– Uploading using the web application
Data Storage
Receipt and employee information is stored in an Azure SQL database.
Documentation
Employees are provided with a getting started document when they first use the solution. The documentation includes details on supported operating systems for Azure File upload, and instructions on how to configure the mounted folder.
Solution details
Users table
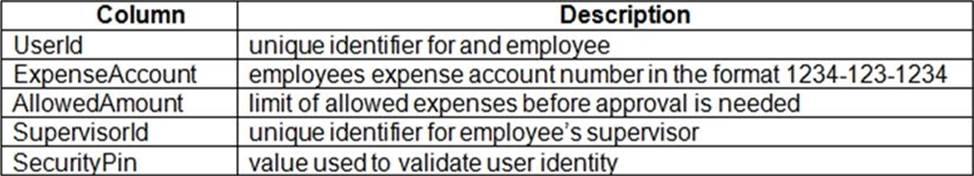
Web Application
You enable MSI for the Web App and configure the Web App to use the security principal name,
Processing
Processing is performed by an Azure Function that uses version 2 of the Azure Function runtime.
Once processing is completed, results are stored in Azure Blob. Storage and an Azure SQL database. Then, an email summary is sent to the user with a link to the processing report. The link to the report must remain valid if the email is forwarded to another user.
Requirements
Receipt processing
Concurrent processing of a receipt must be prevented.
Logging
Azure Application Insights is used for telemetry and logging in both the processor and the web application. The processor also has Trace Writer logging enabled. Application Insights must always contain all log messages.
Disaster recovery
Regional outage must not impact application availability. All DR operations must not be dependent on application running and must ensure that data in the DR region is up to date.
Security
Users’ SecurityPin must be stored in such a way that access to the database does not allow the viewing of SecurityPins. The web application is the only system that should have access to SecurityPins.
All certificates and secrets used to secure data must be stored in Azure Key Vault. You must adhere to the Least Privilege Principal. All access to Azure Storage and Azure SQL database must use the application’s Managed Service Identity (MSI).
Receipt data must always be encrypted at rest.
All data must be protected in transit, User’s expense account number must be visible only to logged in users. All other views of the
expense account number should include only the last segment, with the remaining parts obscured. In the case of a security breach, access to all summary reports must be revoked without impacting other parts of the system.
Issues
Upload format issue
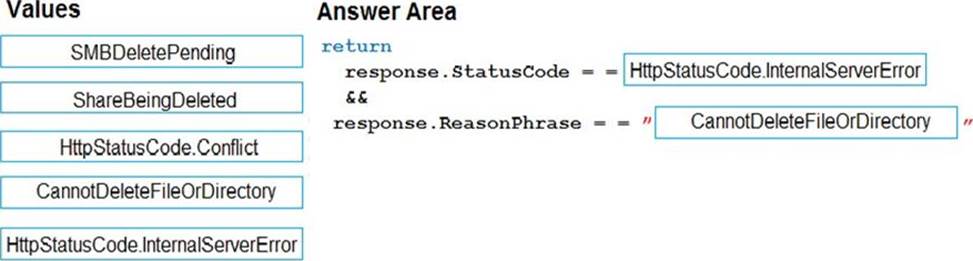
Employees occasionally report an issue with uploading a receipt using the web application. They report that when they upload a receipt using the Azure File Share, the receipt does not appear in their profile. When this occurs, they delete the file in the file share and use the web application, which returns a 500 Internal Server error page.
Capacity issue
During busy periods, employees report long delays between the time they upload the receipt and when it appears in the web application.
Log capacity issue
Developers report that the number of log messages in the trace output for the processor is too high, resulting in lost log messages-
Application code
Processing.cs
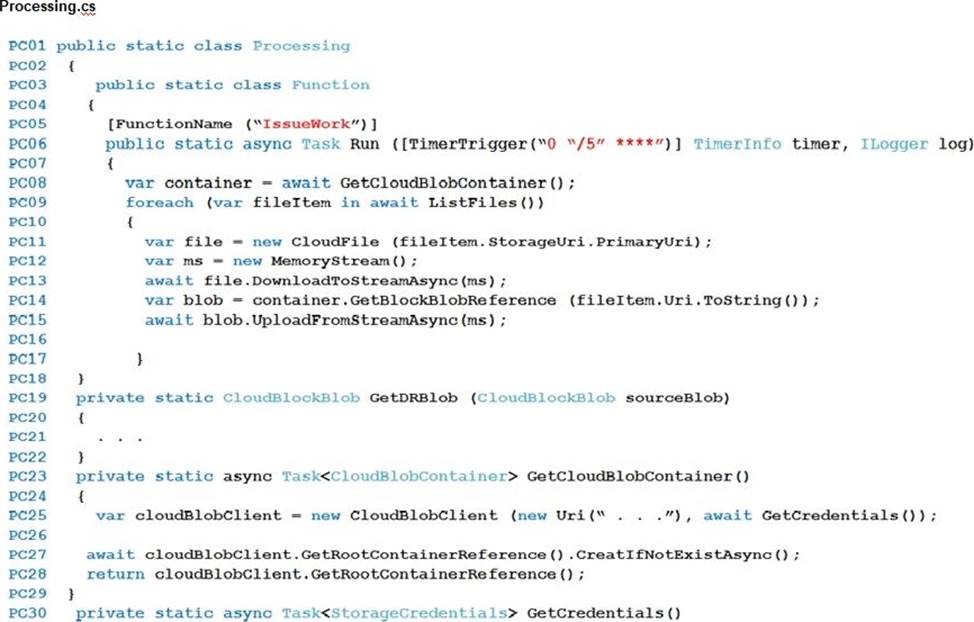
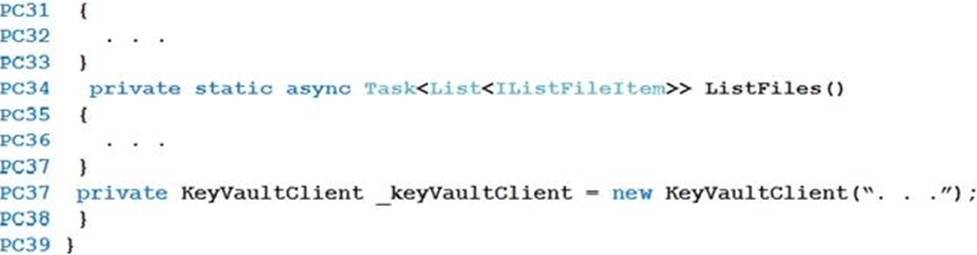
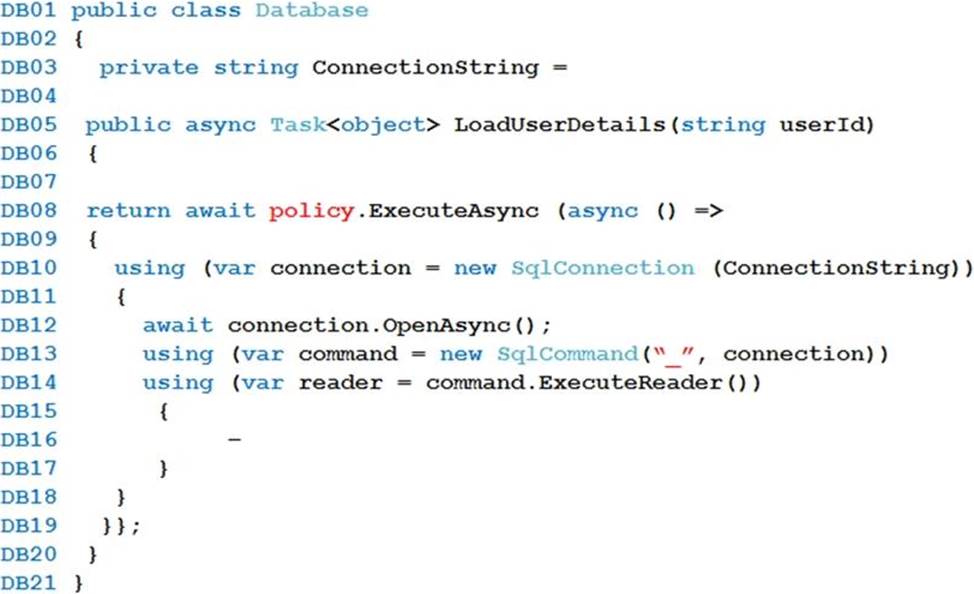
Database.cs
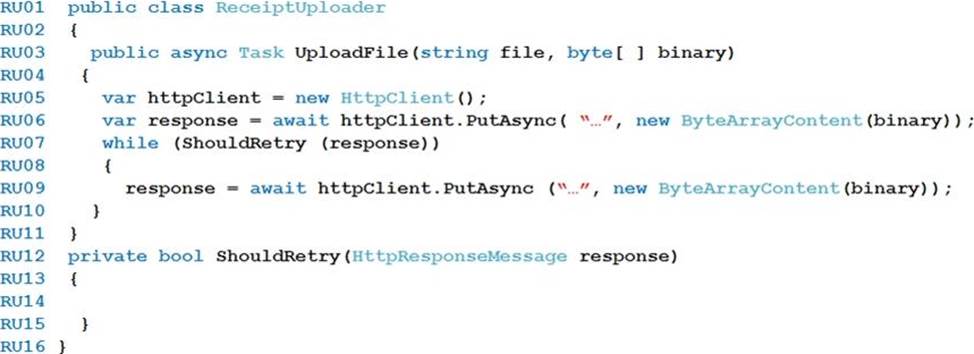
ReceiptUploader.cs
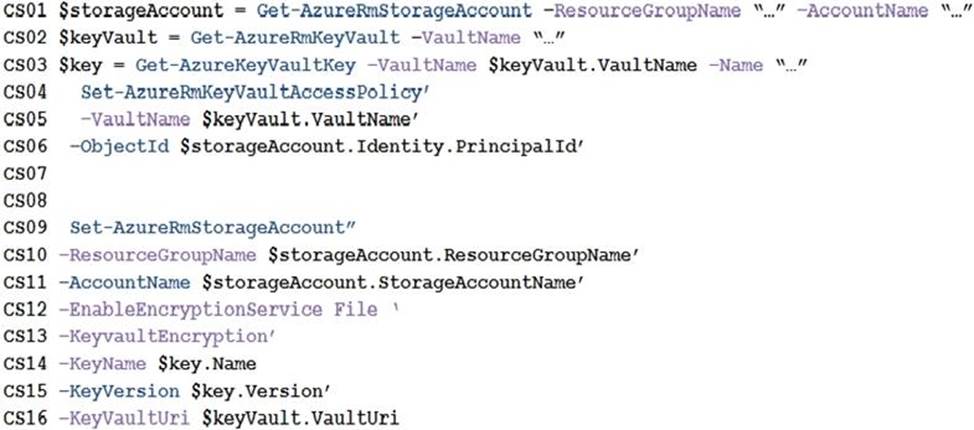
ConfigureSSE.ps1
DRAG DROP
You need to ensure that the upload format issue is resolved.
What code should you add at line RU14? To answer, drag the appropriate code fragments to the correct locations. Each code fragment may
be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT
You need to add the Supporting Operating Systems section to the Getting Started document.
How should you complete the section? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

HOTSPOT
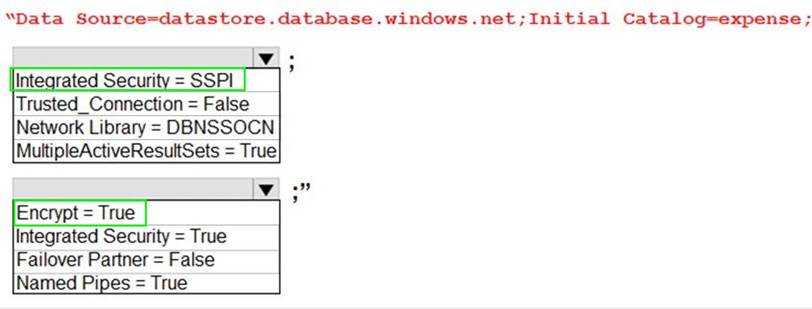
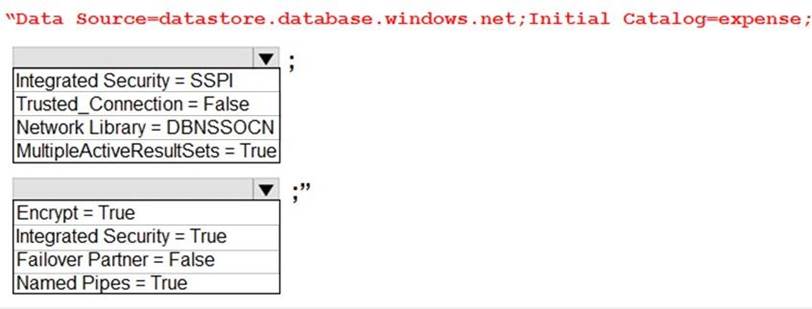
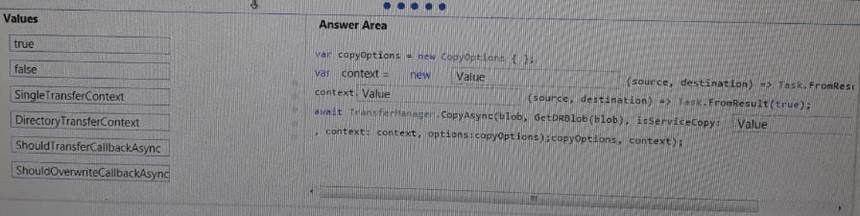
You need to ensure that security requirements are met.
What value should be used for the ConnectionString field on line DB03 in the Database class? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
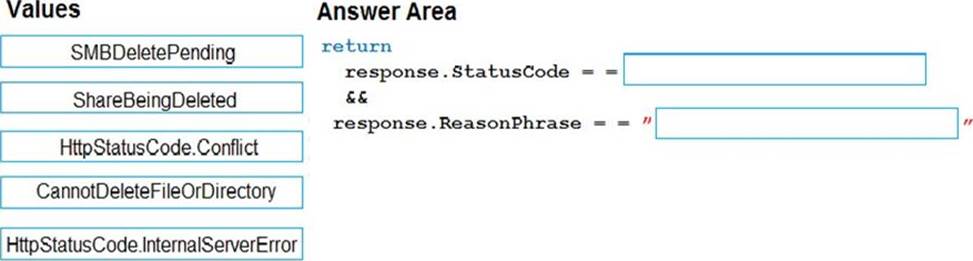
HOTSPOT
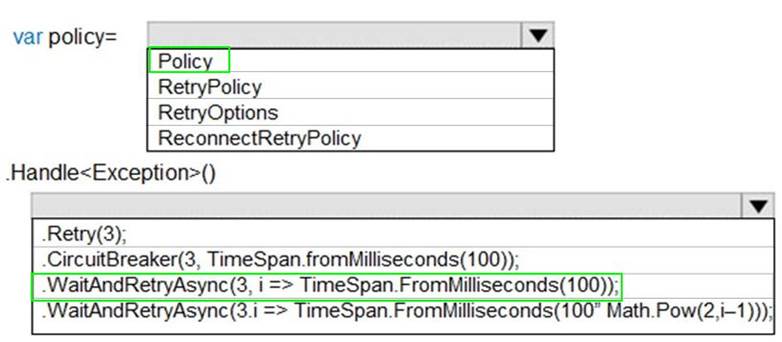
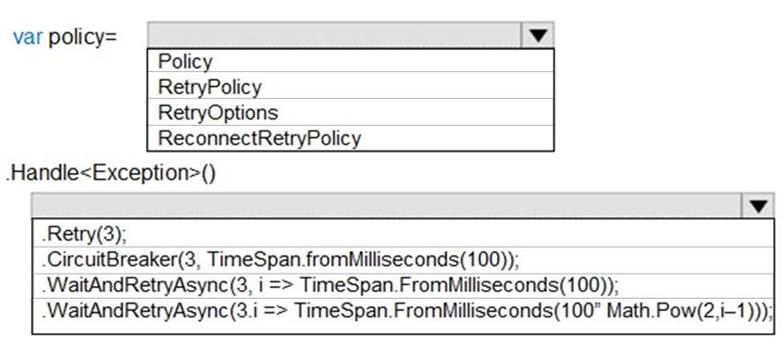
You need to configure retries in the LoadUserDetails function in the Database class without impacting user experience.
What code should you insert on line DB07? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution Determine whether the solution meets the stated goals.
You need to ensure that the SecurityPin security requirements are met.
Solution: Enable Always Encrypted for the SecurityPin column using a certificate based on a trusted certificate authority. Update the Getting Started document with instruction to ensure that the certificate is installed on user machines.
Does the solution meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
You need to ensure that the SecurityPin security requirements are met.
Solution: Enable Always Encrypted for the SecurityPin column using a certificate contained in Azure Key Vault and grant the WebAppIdentity service principal access to the certificate.
Does the solution meet the goal?
- A . Yes
- B . No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution. Determine whether the solution meets the stated goals.
You need to ensure that the SecurityPin security requirements are met. Solution; Using the Azure Portal, add Data Masking to the SecurityPin column, and exclude the dbo user. Add a SQL security policy with a filter predicate based on the user identity.
Does the solution meet the goal?
- A . Yes
- B . No
You need to construct the link to the summary report for the email that is sent to users.
What should you do?
- A . Create a SharedAccessBlobPolicy and add it to the containers SharedAccessPolicies. Call GetSharedAccessSignature on the blob and use the resulting link.
- B . Create a SharedAccessBlobPolicy and set the expiry time to two weeks from today. Call GetSharedAccessSignature on the blob and use the resulting link.
- C . Create a SharedAccessAccountPolicy and call GetsharedAccessSignature on storage account and use the resulting link.
- D . Create a SharedAccessBlobPolicy and set the expiry time to two weeks from today. Call GetSharedAccessSignature on the container and use the resulting link.
DRAG DROP
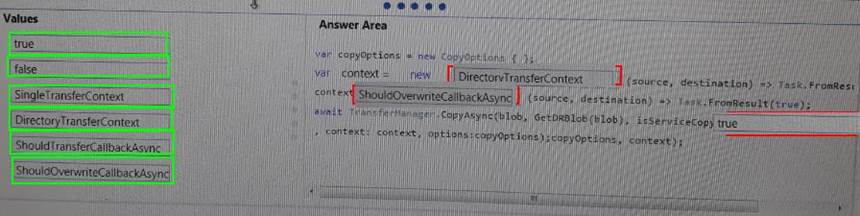
You need to ensure disaster recovery requirements are met.
What code should you add at line PC16? To answer, drag the appropriate code fragments to the correct locations. Each code fragment may
be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
You need to resolve the log capacity issue.
What should you do?
- A . Implement Application Insights Sampling.
- B . Change the minimum log level in the host.json file for the function.
- C . Create an Application Insights Telemetry Filter.
- D . Set a LogCategoryFilter during startup.
Latest AZ-202 Dumps Valid Version with 150 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund