How should you configure network security?
Topic 2, Contoso, Ltd
Case study
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. When you are ready to answer a question, click the Question button to return to the question.
Background
Overview
You are a developer for Contoso, Ltd. The company has a social networking website that is developed as a Single Page Application (SPA). The main web application for the social networking website loads user uploaded content from blob storage.
You are developing a solution to monitor uploaded data for inappropriate content.
The following process occurs when users upload content by using the SPA:
• Messages are sent to ContentUploadService.
• Content is processed by ContentAnalysisService.
• After processing is complete, the content is posted to the social network or a rejection message is posted in its place.
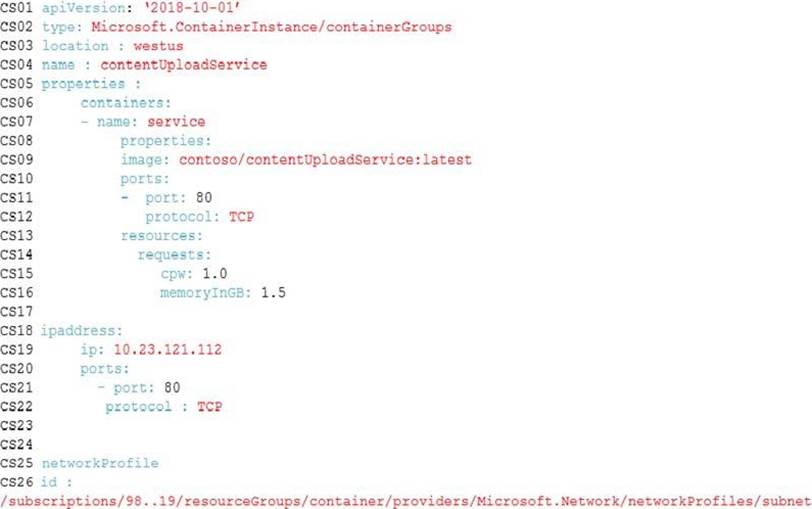
The ContentAnalysisService is deployed with Azure Container Instances from a private Azure Container Registry named contosoimages.
The solution will use eight CPU cores.
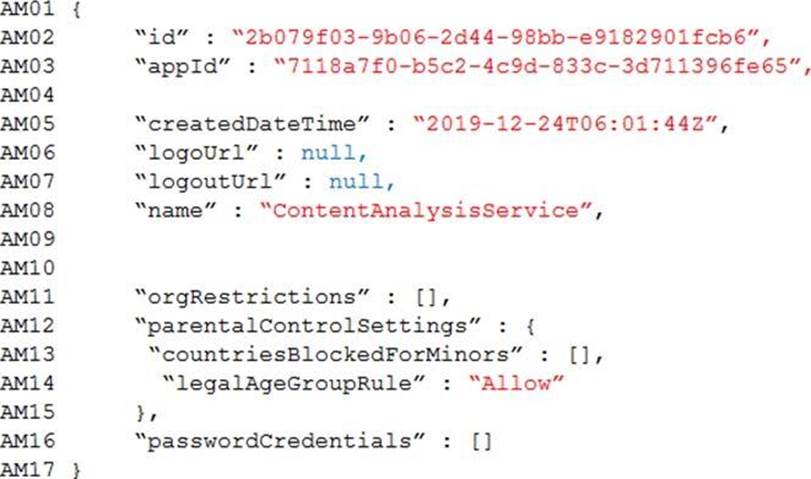
Azure Active Directory
Contoso, Ltd. uses Azure Active Directory (Azure AD) for both internal and guest accounts.
Requirements
ContentAnalysisService
The company’s data science group built ContentAnalysisService which accepts user generated content as a string and returns a probable value for inappropriate content. Any values over a specific threshold must be reviewed by an employee of Contoso, Ltd.
You must create an Azure Function named CheckUserContent to perform the content checks.
Costs
You must minimize costs for all Azure services.
Manual review
To review content, the user must authenticate to the website portion of the ContentAnalysisService using their Azure AD credentials. The website is built using React and all pages and API endpoints require authentication. In order to review content a user must be part of a ContentReviewer role. All completed reviews must include the reviewer’s email address for auditing purposes.
High availability
All services must run in multiple regions. The failure of any service in a region must not impact overall application availability.
Monitoring
An alert must be raised if the ContentUploadService uses more than 80 percent of available CPU cores.
Security
You have the following security requirements:
– Any web service accessible over the Internet must be protected from cross site scripting attacks.
– All websites and services must use SSL from a valid root certificate authority.
– Azure Storage access keys must only be stored in memory and must be available only to the service.
– All Internal services must only be accessible from internal Virtual Networks (VNets).
– All parts of the system must support inbound and outbound traffic restrictions.
– All service calls must be authenticated by using Azure AD.
User agreements
When a user submits content, they must agree to a user agreement. The agreement allows employees of Contoso, Ltd. to review content, store cookies on user devices, and track user’s IP addresses.
Information regarding agreements is used by multiple divisions within Contoso, Ltd.
User responses must not be lost and must be available to all parties regardless of individual service uptime. The volume of agreements is expected to be in the millions per hour.
Validation testing
When a new version of the ContentAnalysisService is available the previous seven days of content must be processed with the new version to verify that the new version does not significantly deviate from the old version.
Issues
Users of the ContentUploadService report that they occasionally see HTTP 502 responses on specific pages.
Code
ContentUploadService
HOTSPOT
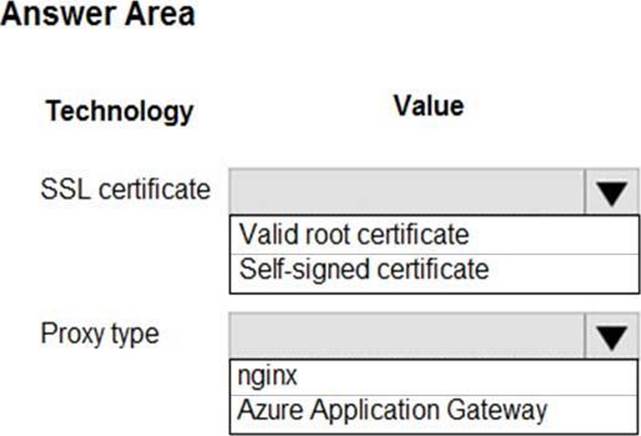
You need to ensure that network security policies are met.
How should you configure network security? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Answer: 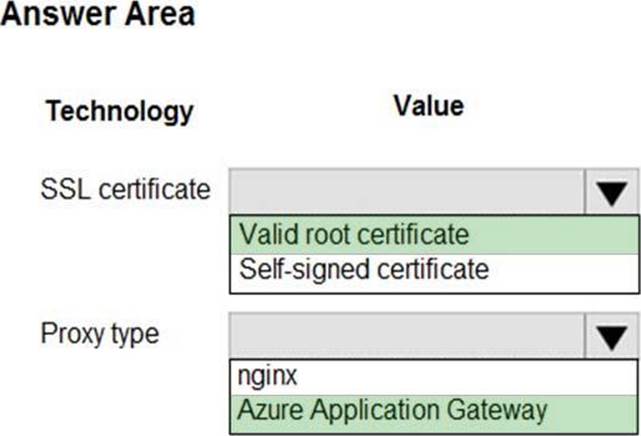
Explanation:
Box 1: Valid root certificate
Scenario: All websites and services must use SSL from a valid root certificate authority.
Box 2: Azure Application Gateway
Scenario:
✑ Any web service accessible over the Internet must be protected from cross site scripting attacks.
✑ All Internal services must only be accessible from Internal Virtual Networks (VNets)
✑ All parts of the system must support inbound and outbound traffic restrictions.
Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities. Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities. SQL injection and cross-site scripting are among the most common attacks.
Application Gateway supports autoscaling, SSL offloading, and end-to-end SSL, a web application firewall (WAF), cookie-based session affinity, URL path-based routing, multisite hosting, redirection, rewrite HTTP headers and other features. NOTE: Both Nginx and Azure Application Gateway act as a reverse proxy with Layer 7 loadbalancing features plus a WAF to ensure strong protection against common web vulnerabilities and exploits.
You can modify Nginx web server configuration/SSL for X-XSS protection. This helps to prevent cross-site scripting exploits by forcing the injection of HTTP headers with X-XSS protection.
Latest AZ-204 Dumps Valid Version with 254 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

