Drag and drop the threat from the left onto the scenario that introduces the threat on the right. Not all options are used
DRAG DROP
Drag and drop the threat from the left onto the scenario that introduces the threat on the right. Not all options are used.
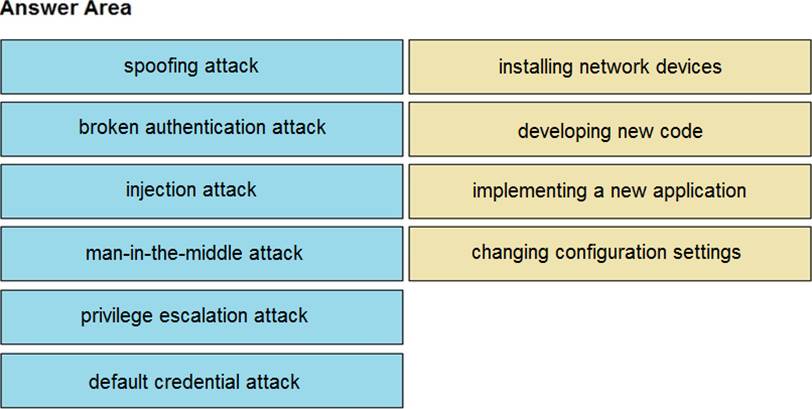
Answer: 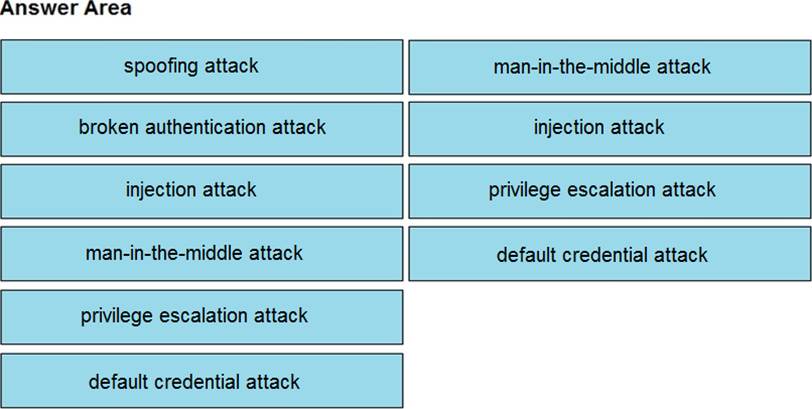
Latest 350-201 Dumps Valid Version with 139 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund


STOP SHARING WRONG ANSWERS!!!!!!!!
Man-in-the-middle – Installing network device
Injection attack – developing new code
Default credential – Implementing a new application
Privilege escalation attack – Changing configuration settings