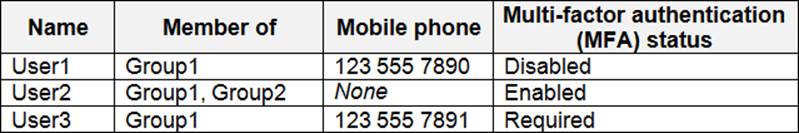
You have an Azure Active Directory (Azure AD) ten ant named contoso.com that contains the u sers shown in the following table
HOTSPOT
You create and enforce an Azure AD Identity Protection user risk policy that has the following settings:
– Assignment: Include Group1, Exclude Group2
– Conditions: Sign-in risk of Medium and above
– Access: Allow access, Require password change
You have an Azure Active Directory (Azure AD) ten ant named contoso.com that contains the u sers shown in the following table.
You create and enforce an Azure AD Identity Protection user risk policy that has the following settings:
• Assignment: Include Group1, Exclude Group2
• Conditions: Sign-in risk of Medium and above
• Access: Allow access, Require password change
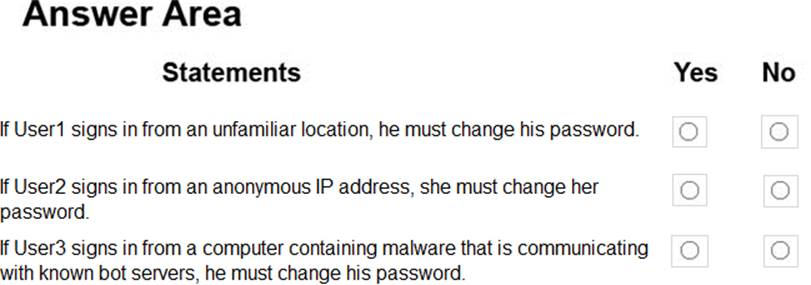
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Answer: 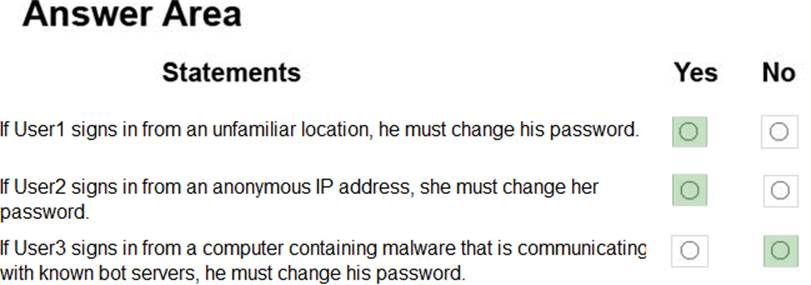
Explanation:
Box 1: Yes
User1 is member of Group1. Sign in from unfamiliar location is risk level Medium.
Box 2: Yes
User2 is member of Group1. Sign in from anonymous IP address is risk level Medium.
Box 3: No
Sign-ins from IP addresses with suspicious activity is low.
Note:
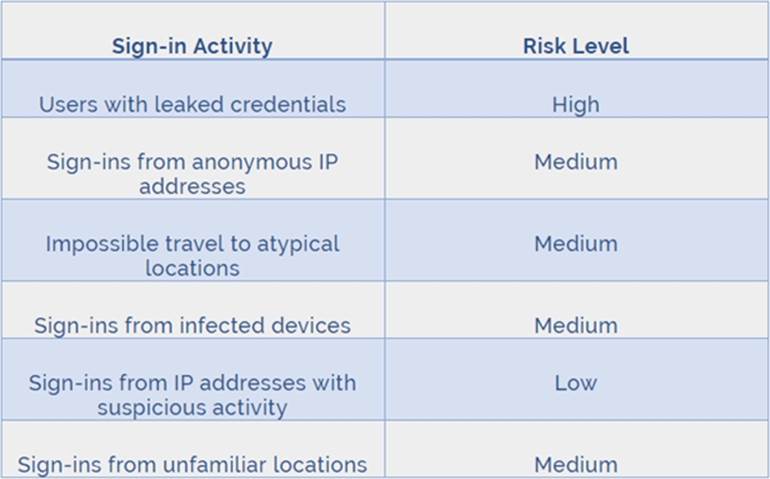
Azure AD Identity protection can detect six types of suspicious sign-in activities:
• Users with leaked credentials
• Sign-ins from anonymous IP addresses
• Impossible travel to atypical locations
• Sign-ins from infected devices
• Sign-ins from IP addresses with suspicious activity
• Sign-ins from unfamiliar locations
These six types of events are categorized in to 3 levels of risks C High, Medium & Low:
References: http://www.rebeladmin.com/2018/09/step-step-guide-configure-risk-based-azure-conditional-access-policies/
Latest AZ-500 Dumps Valid Version with 278 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

