Palo Alto Networks PCNSE6 Palo Alto Networks Certified Network Security Engineer 6 Online Training
Palo Alto Networks PCNSE6 Online Training
The questions for PCNSE6 were last updated at Feb 07,2026.
- Exam Code: PCNSE6
- Exam Name: Palo Alto Networks Certified Network Security Engineer 6
- Certification Provider: Palo Alto Networks
- Latest update: Feb 07,2026
Configuring a pair of devices into an Active/Active HA pair provides support for:
- A . Higher session count
- B . Redundant Virtual Routers
- C . Asymmetric routing environments
- D . Lower fail-over times
As a Palo Alto Networks firewall administrator, you have made unwanted changes to the Candidate configuration.
These changes may be undone by Device > Setup > Operations > Configuration Management>….and then what operation?
- A . Revert to Running Configuration
- B . Revert to last Saved Configuration
- C . Load Configuration Version
- D . Import Named Configuration Snapshot
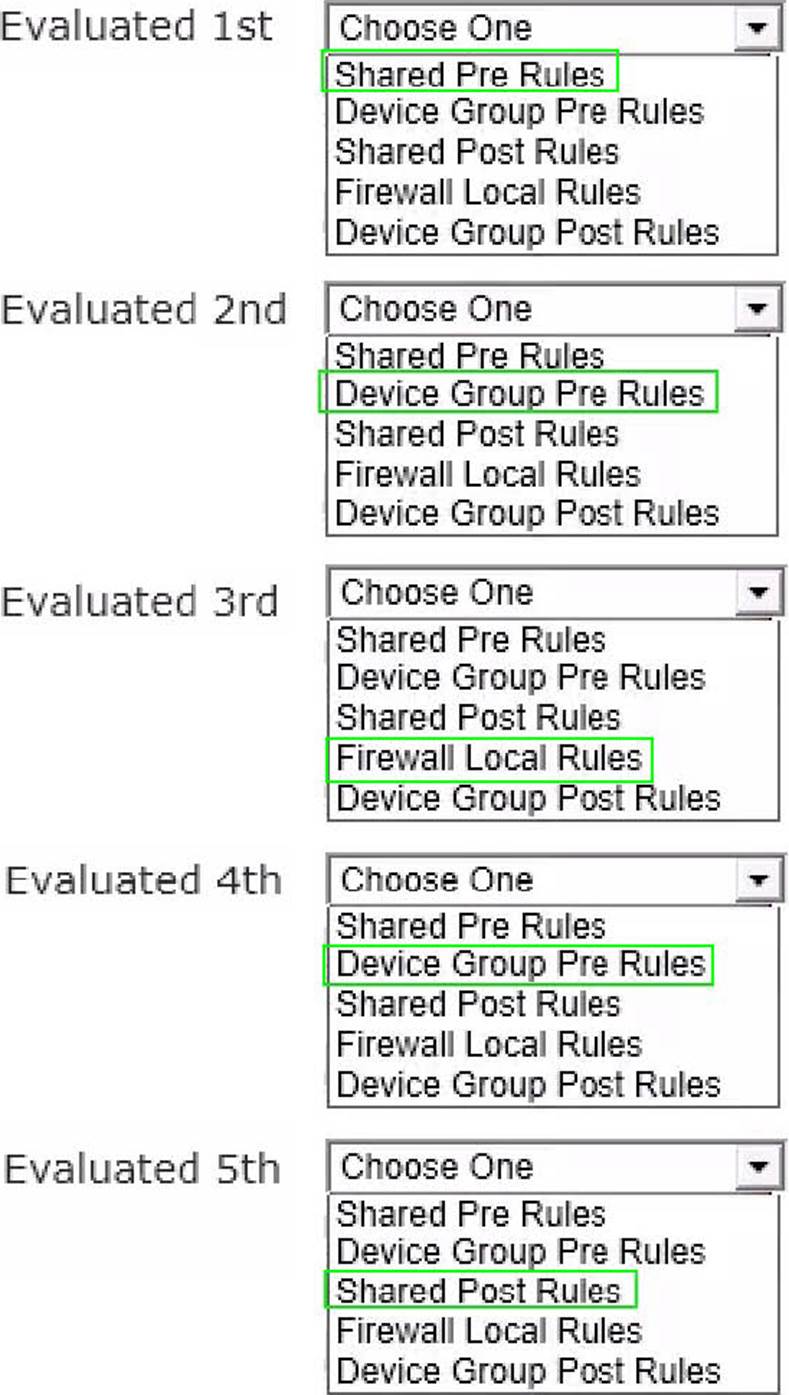
A company has a Palo Alto Networks firewall with a single VSYS that has both locally defined rules as well as shared and device-group rules pushed from Panorama.
In what order are the policies evaluated?
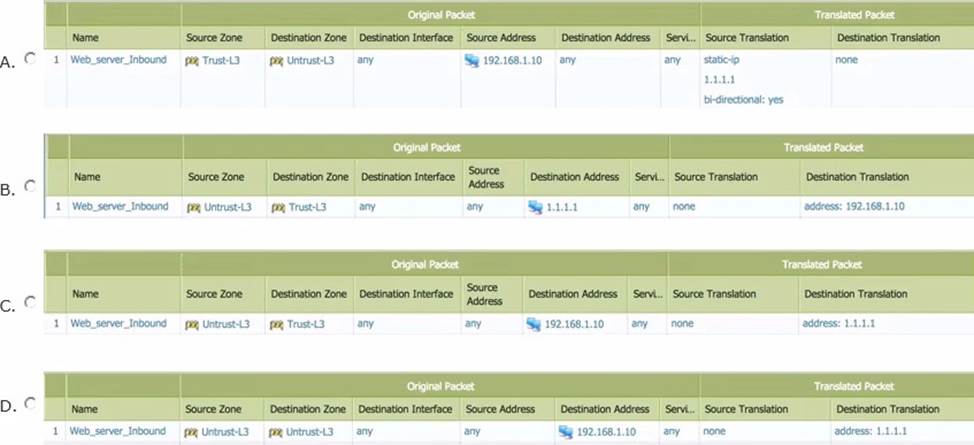
A company hosts a publicly-accessible web server behind their Palo Alto Networks firewall, with this configuration information:
Users outside the company are in the "Untrust-L3" zone. The web server physically resides in the "Trust-L3" zone. Web server public IP address: 1.1.1.1
Web server private IP address: 192.168.1.10
Which NAT Policy rule will allow users outside the company to access the web server?
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Wildfire may be used for identifying which of the following types of traffic?
- A . URL content
- B . DHCP
- C . DNS
- D . Viruses
In PAN-OS 5.0, how is Wildfire enabled?
- A . Via the "Forward" and "Continue and Forward" File-Blocking actions
- B . A custom file blocking action must be enabled for all PDF and PE type files
- C . Wildfire is automatically enabled with a valid URL-Filtering license
- D . Via the URL-Filtering "Continue" Action.
The IT department has received complaints about VoIP call jitter when the sales staff is making or receiving calls. QoS is enabled on all firewall interfaces, but there is no QoS policy written in the rulebase. The IT manager wants to find out what traffic is causing the jitter in real time when a user reports the jitter.
Which feature can be used to identify, in real-time, the applications taking up the most bandwidth?
- A . Application Command Center (ACC)
- B . QoS Statistics
- C . QoS Log
- D . Applications Report
Which two steps are required to make Microsoft Active Directory users appear in the firewall’s traffic log? Choose 2 answers
- A . Enable User-ID on the zone object for the source zone.
- B . Enable User-ID on the zone object for the destination zone.
- C . Configure a RADIUS server profile to point to a domain controller.
- D . Run the User-ID Agent using an Active Directory account that has "domain administrator" permissions.
- E . Run the User-ID Agent using an Active Directory account that has "event log viewer" permissions.
Administrative Alarms can be enabled for which of the following except?
- A . Certificate Expirations
- B . Security Violation Thresholds
- C . Security Policy Tags
- D . Traffic Log capacity
Where in the firewall GUI can an administrator see how many sessions of web-browsing traffic have occurred in the last day?
- A . Monitor->Session Browser
- B . Monitor->App Scope->Summary
- C . Objects->Applications->web-browsing
- D . ACC->Application
Latest PCNSE6 Dumps Valid Version with 153 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund