Palo Alto Networks PCNSA Palo Alto Networks Certified Network Security Administrator Online Training
Palo Alto Networks PCNSA Online Training
The questions for PCNSA were last updated at Feb 08,2026.
- Exam Code: PCNSA
- Exam Name: Palo Alto Networks Certified Network Security Administrator
- Certification Provider: Palo Alto Networks
- Latest update: Feb 08,2026
Where in Panorama would Zone Protection profiles be configured?
- A . Templates
- B . Device Groups
- C . Shared
- D . Panorama tab
A
Explanation:
Create a Zone Protection profile for the firewalls in the data center template (T_DataCenter). Select the Network tab and, in the Template drop-down, select T_DataCenter.
Select Network ProfilesZone Protection and click Add.
An administrator wants to prevent access to media content websites that are risky.
Which two URL categories should be combined in a custom URL category to accomplish this goal? (Choose two.)
- A . recreation-and-hobbies
- B . streaming-media
- C . known-risk
- D . high-risk
BD
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/content-inspection-features/url-filtering-multi-category.html
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-new-features/content-inspection-features/url-filtering-security-categories.html
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can run malicious code against a targeted machine.
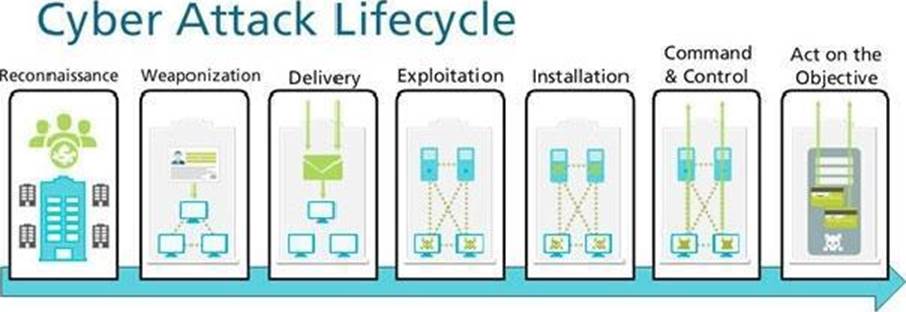
- A . Exploitation
- B . Installation
- C . Reconnaissance
- D . Act on Objective
A
Explanation:
https://www.paloaltonetworks.com/cyberpedia/how-to-break-the-cyber-attack-lifecycle
According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
- A . by minute
- B . hourly
- C . daily
- D . weekly
C
Explanation:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/threat-prevention/best-practices-for-content-and-threat-content-updates/best-practices-mission-critical.html
An address object of type IP Wildcard Mask can be referenced in which part of the configuration?
- A . Security policy rule
- B . ACC global filter
- C . external dynamic list
- D . NAT address pool
A
Explanation:
You can use an address object of type IP Wildcard Mask only in a Security policy rule. https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-web-interface-help/objects/objects-addresses IP Wildcard Mask
–Enter an IP wildcard address in the format of an IPv4 address followed by a slash and a mask (which must begin with a zero); for example, 10.182.1.1/0.127.248.0. In the wildcard mask, a zero (0) bit indicates that the bit being compared must match the bit in the IP address that is covered by the 0. A one (1) bit in the mask is a wildcard bit, meaning the bit being compared need not match the bit in the IP address that is covered by the 1. Convert the IP address and the wildcard mask to binary. To illustrate the matching: on binary snippet 0011, a wildcard mask of 1010 results in four matches (0001, 0011, 1001, and 1011).
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
- A . SAML
- B . TACACS+
- C . LDAP
- D . Kerberos
AB
Explanation:
The administrative accounts are defined on an external SAML, TACACS+, or RADIUS server.
The server performs both authentication and authorization. For authorization, you define Vendor-Specific Attributes (VSAs) on the TACACS+ or RADIUS server, or SAML attributes on the SAML server. PAN-OS maps the attributes to administrator roles, access domains, user groups, and virtual systems that you define on the firewall.
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/firewall-administration/manage-
firewall-administrators/administrative-authentication.html
What do you configure if you want to set up a group of objects based on their ports alone?
- A . address groups
- B . custom objects
- C . application groups
- D . service groups
D
Explanation:
Service = layer 4, Application = layer 7
A Security Profile can block or allow traffic at which point?
- A . after it is matched to a Security policy rule that allows traffic
- B . on either the data plane or the management plane
- C . after it is matched to a Security policy rule that allows or blocks traffic
- D . before it is matched to a Security policy rule
A
Explanation:
Security Profiles are added to the end of Security policy rules. After a packet has been allowed by the Security policy.
Which three filter columns are available when setting up an Application Filter? (Choose three.)
- A . Parent App
- B . Category
- C . Risk
- D . Standard Ports
- E . Subcategory
BCE
Explanation:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-web-interface-help/objects/objects-application-filters
What are three factors that can be used in domain generation algorithms? (Choose three.)
- A . cryptographic keys
- B . time of day
- C . other unique values
- D . URL custom categories
- E . IP address
ABC
Explanation:
Domain generation algorithms (DGAs) are used to auto-generate domains, typically in large numbers within the context of establishing a malicious command-and-control (C2) communications channel. DGA-based malware (such as Pushdo, BankPatch, and CryptoLocker) limit the number of domains from being blocked by hiding the location of their active C2 servers within a large number of possible
suspects, and can be algorithmically generated based on factors such as time of day, cryptographic keys, or other unique values.
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/threat-prevention/dns-security/domain-generation-algorithm-detection
Latest PCNSA Dumps Valid Version with 115 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

