Fortinet FCSS_EFW_AD-7.4 FCSS – Enterprise Firewall 7.4 Administrator Online Training
Fortinet FCSS_EFW_AD-7.4 Online Training
The questions for FCSS_EFW_AD-7.4 were last updated at Feb 06,2026.
- Exam Code: FCSS_EFW_AD-7.4
- Exam Name: FCSS - Enterprise Firewall 7.4 Administrator
- Certification Provider: Fortinet
- Latest update: Feb 06,2026
An administrator must ensure that users cannot access sites containing malware and spyware, while also protecting them from phishing attempts.
What is the most resource-efficient method to block access to these sites?
- A . Enable antivirus profiles to scan all web traffic and block downloads from these malicious sites.
- B . Configure FortiGuard Web Filtering and block the categories malware, spyware, and phishing to prevent access to such sites.
- C . Create a custom IPS policy to monitor and block all outbound traffic related to malware, spyware, and phishing sites.
- D . Set up a DNS filter and block domains related to these categories to stop users from reaching malicious content.
What global configuration setting changes the behavior for content-inspected traffic while FortiGate is in system conserve mode?
- A . av-failopen
- B . mem-failopen
- C . utm-failopen
- D . ips-failopen
Examine the following traffic log; then answer the question below.
date-20xx-02-01 time=19:52:01 devname=masterdevice_id="xxxxxxx" log_id=0100020007 type=event subtype=system pri critical vd=root service=kemel status=failure msg="NAT port is exhausted."
What does the log mean?
- A . There is not enough available memory in the system to create a new entry in the NAT port table.
- B . The limit for the maximum number of simultaneous sessions sharing the same NAT port has been reached.
- C . FortiGate does not have any available NAT port for a new connection.
- D . The limit for the maximum number of entries in the NAT port table has been reached.
Refer to the exhibit, which contains partial output from an IKE real-time debug.
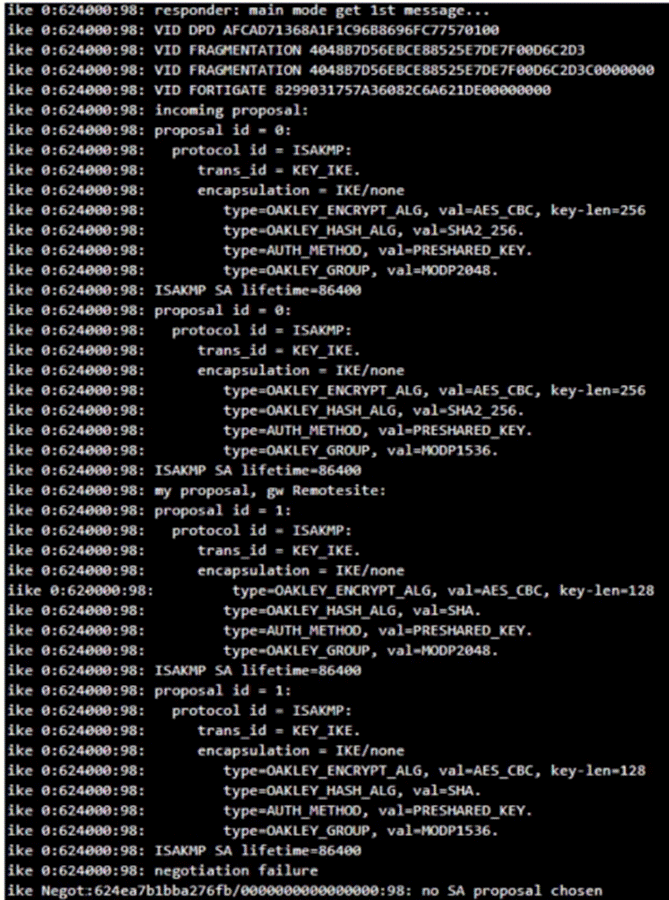
The administrator does not have access to the remote gateway.
Based on the debug output, which configuration change can the administrator make to the local gateway to resolve the phase 1 negotiation error?
- A . In the phase 1 network configuration, set the IKE version to 2.
- B . In the phase 1 proposal configuration, add AES128-SHA128 to the list of encryption algorithms.
- C . In the phase 1 proposal configuration, add AESCBC-SHA2 to the list of encryption algorithms.
- D . In the phase 1 proposal configuration, add AES256-SHA256 to the list of encryption algorithms.
Refer to the exhibit, which shows a partial web filter profile configuration.
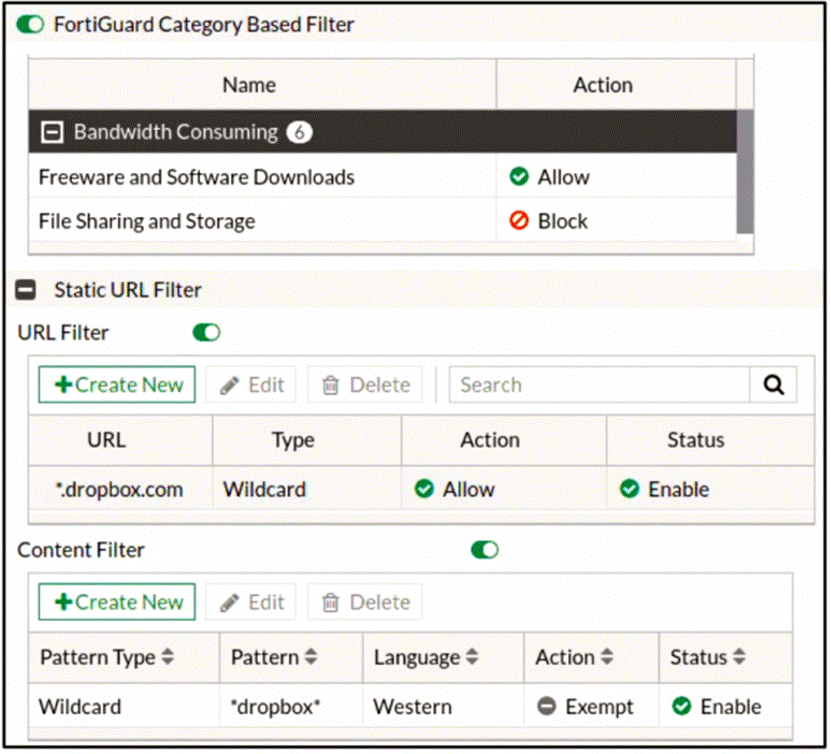
Which action will FortiGate take if a user attempts to access www.dropbox.com, which is categorized as File Sharing and Storage?
- A . FortiGate will block the connection, based on the FortiGuard category based filter configuration.
- B . FortiGate will block the connection as an invalid URL.
- C . FortiGate will exempt the connection, based on the Web Content Filter configuration.
- D . FortiGate will allow the connection, based onthe URL Filter configuration.
Refer to the exhibit, which shows partial outputs from two routing debug commands.
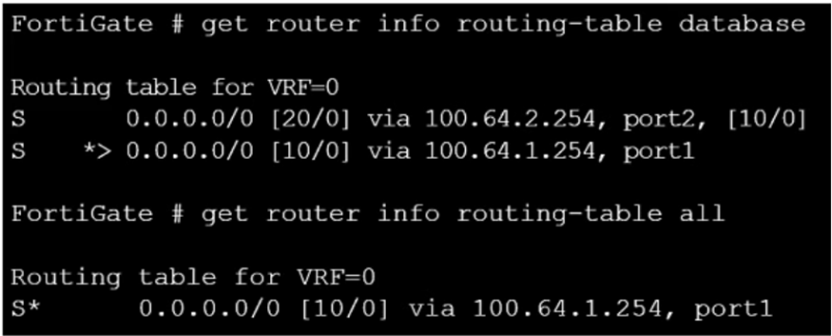
Why is the port2 default route not in the second command output?
- A . The port2 interface is disabled in the FortiGate configuration.
- B . The port1 default route has a lower distance than the default route using port2.
- C . The port1 default route has a higher priority value than the default route using port2.
- D . The port1 default route has a lower priority value than the default route using port2.
How does FortiManager handle FortiGuard requests from FortiGate devices, when it is configured as a local FDS?
- A . FortiManager can download and maintain local copies of FortiGuard databases.
- B . FortiManager supports only FortiGuard push to managed devices.
- C . FortiManager will respond to update requests only if they originate from a managed device.
- D . FortiManager does not support rating requests.
An administrator has configured a dial-up IPsec VPN with one phase 2, extended authentication (XAuth) and IKE mode configuration.
The administrator has also enabled the IKE real time debug:
diagnose debug application ike-1
diagnose debug enable
In which order is each step and phase displayed in the debug output each time a new dial-up user is connecting to the VPN?
- A . Phase1; IKE mode configuration; XAuth; phase 2.
- B . Phase1; XAuth; IKE mode configuration; phase2.
- C . Phase1; XAuth; phase 2; IKE mode configuration.
- D . Phase1; IKE mode configuration; phase 2; XAuth.
View the exhibit, which contains the partial output of a diagnose command, and then answer the question below.
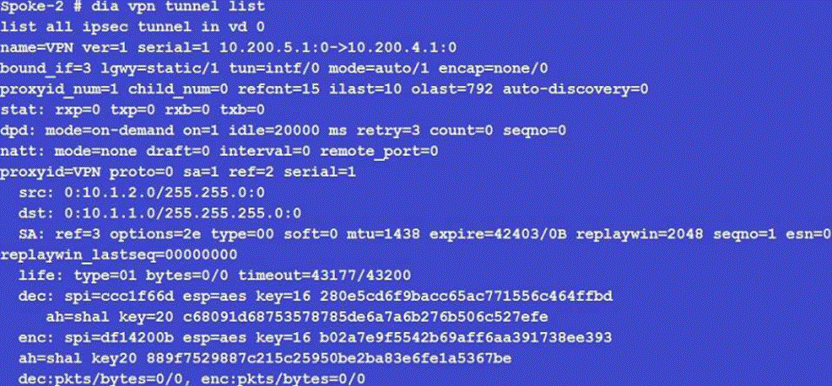
Based on the output, which of the following statements is correct?
- A . Anti-replay is enabled.
- B . DPD is disabled.
- C . Quick mode selectors are disabled.
- D . Remote gateway IP is 10.200.5.1.
Which statement about the designated router (DR) and backup designated router (BDR) in an OSPF multi-access network is true?
- A . Only the DR receives link state information from non-DR routers.
- B . Non-DR and non-BDR routers form full adjacencies to DR only.
- C . Non-DR and non-BDR routers send link state updates and acknowledgements to 224.0.0.6.
- D . FortiGate first checks the OSPF ID to elect a DR.
Latest FCSS_EFW_AD-7.4 Dumps Valid Version with 210 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

