Fortinet FCP_FML_AD-7.4 FCP – FortiMail 7.4 Administrator Online Training
Fortinet FCP_FML_AD-7.4 Online Training
The questions for FCP_FML_AD-7.4 were last updated at Feb 10,2026.
- Exam Code: FCP_FML_AD-7.4
- Exam Name: FCP - FortiMail 7.4 Administrator
- Certification Provider: Fortinet
- Latest update: Feb 10,2026
Which traditional SMTP encryption method is commonly used to secure email transmission between servers?
- A . HTTPS
- B . S/MIME
- C . TLS (Transport Layer Security)
- D . SSH
Which part of the email header contains the recipient’s email address?
- A . To field
- B . CC field
- C . From field
- D . Subject field
Refer to the exhibit which displays the domain configuration of a transparent mode FortiMail device.
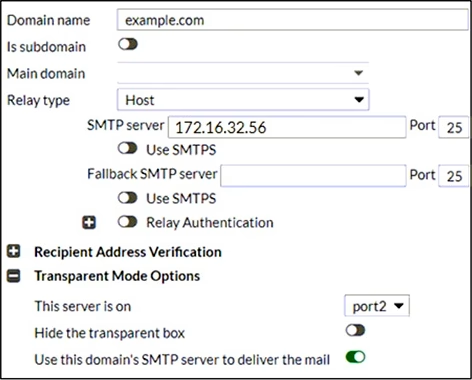
Based on the exhibit, which two sessions are considered incoming sessions? (Choose two.)
- A . DESTINATION IP: 172.16.32.56 MAIL FROM: [email protected] RCPT TO: [email protected]
- B . DESTINATION IP: 192.168.54.10 MAIL FROM: [email protected] RCPT TO: [email protected]
- C . DESTINATION IP: 10.25.32.15 MAIL FROM: [email protected] RCPT TO: [email protected]
- D . DESTINATION IP: 172.16.32.56 MAIL FROM: [email protected] RCPT TO: [email protected]
What is the primary goal of email security in the context of network communication?
- A . Increasing email delivery speed
- B . Encrypting email attachments
- C . Ensuring the confidentiality and integrity of email communication
- D . Reducing the size of email attachments
When deploying FortiMail in transparent mode, which of the following statements are true? (Select all that apply)
- A . FortiMail acts as an intermediary for email traffic.
- B . Email attachments are automatically encrypted.
- C . Transparent mode requires changes to the mail server’s IP address.
- D . FortiMail’s functions are hidden from the email server.
- E . Transparent mode is suitable for organizations with complex email infrastructures.
Which two statements describe the push delivery method used by IBE? (Choose two.)
- A . Decrypted email is displayed using the HTTPS webmail interface.
- B . FortiMail generates a notification email message with an embedded HTTPS URL.
- C . FortiMail encrypts the email and adds it to a notification email as an HTML attachment.
- D . The recipient accesses the HTTPS link and logs in to the FortiMail secure message portal.
What is the benefit of session-based email filtering over traditional end-point scanning?
- A . It reduces the load on email servers.
- B . It allows for larger email attachments.
- C . It scans emails in real-time, preventing potential threats before they enter the network.
- D . It reduces the likelihood of false positives.
Refer to the exhibit which shows the Authentication Reputation list on a gateway mode FortiMail device.
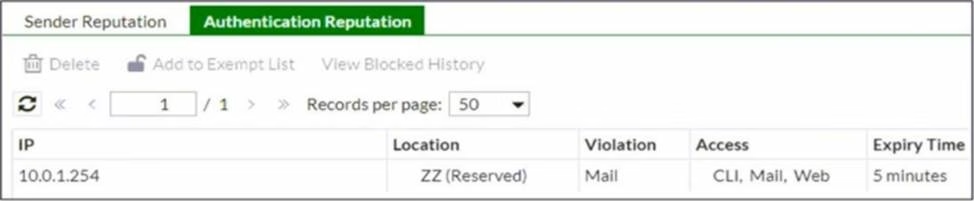
Why was the IP address blocked?
- A . The IP address had consecutive administrative password failures to FortiMai
- B . The IP address had consecutive SMTPS login failures to FortiMail.
- C . The IP address had consecutive SSH, SMTPS, and HTTPS login failures to FortiMail.
- D . The IP address had consecutive IMAP login failures to FortiMail
Which tool or feature in FortiMail would you use to identify email traffic patterns and potential anomalies?
- A . FortiAnalyzer
- B . FortiGate
- C . FortiMail Manager
- D . FortiSwitch
Refer to the exhibit which displays a history log entry.
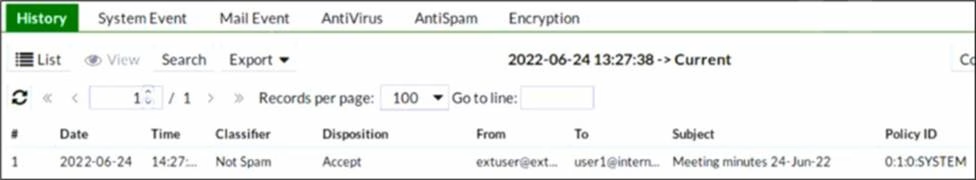
Why does the last field show SYSTEM in the Policy ID column?
- A . The email was dropped by a system blocklist.
- B . It is an inbound email.
- C . The email matched a system-level authentication policy.
- D . The email did not match a recipient-based policy.
Latest FCP_FML_AD-7.4 Dumps Valid Version with 135 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

