ISA ISA-IEC-62443 ISA/IEC 62443 Cybersecurity Fundamentals Specialist Online Training
ISA ISA-IEC-62443 Online Training
The questions for ISA-IEC-62443 were last updated at Feb 08,2026.
- Exam Code: ISA-IEC-62443
- Exam Name: ISA/IEC 62443 Cybersecurity Fundamentals Specialist
- Certification Provider: ISA
- Latest update: Feb 08,2026
Which of the following is an element of monitoring and improving a CSMS?
Available Choices (select all choices that are correct)
- A . Increase in staff training and security awareness
- B . Restricted access to the industrial control system to an as-needed basis
- C . Significant changes in identified risk round in periodic reassessments
- D . Review of system logs and other key data files
Which of the following attacks relies on a human weakness to succeed?
Available Choices (select all choices that are correct)
- A . Denial-of-service
- B . Phishing
- C . Escalation-of-privileges
- D . Spoofing
What is a feature of an asymmetric key?
Available Choices (select all choices that are correct)
- A . Uses a continuous stream
- B . Uses different keys
- C . Shares the same key OD.
- D . Has lower network overhead
Which of the following is an example of separation of duties as a part of system development and maintenance?
Available Choices (select all choices that are correct)
- A . Changes are approved by one party and implemented by another.
- B . Configuration settings are made by one party and self-reviewed using a checklist.
- C . Developers write and then test their own code.
- D . Design and implementation are performed by the same team.
Which is an important difference between IT systems and IACS?
Available Choices (select all choices that are correct)
- A . The IACS security priority is integrity.
- B . The IT security priority is availability.
- C . IACS cybersecurity must address safety issues.
- D . Routers are not used in IACS networks.
What is the name of the missing layer in the Open Systems Interconnection (OSI) model shown below?
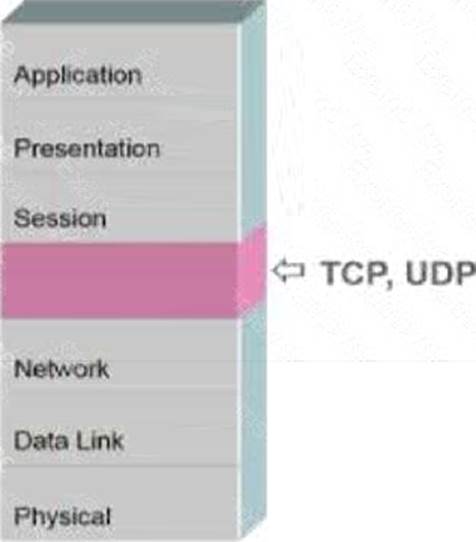
- A . Control
- B . Protocol
- C . Transport
- D . User
What are the four main categories for documents in the ISA-62443 (IEC 62443) series?
Available Choices (select all choices that are correct)
- A . General. Policies and Procedures. System, and Component
- B . End-User, Integrator, Vendor, and Regulator
- C . Assessment. Mitigation. Documentation, and Maintenance
- D . People. Processes. Technology, and Training
Safety management staff are stakeholders of what security program development?
Available Choices (select all choices that are correct)
- A . CSMS
- B . SPRP
- C . CSA
- D . ERM
What does the abbreviation CSMS round in ISA 62443-2-1 represent?
Available Choices (select all choices that are correct)
- A . Control System Management System
- B . Control System Monitoring System
- C . Cyber Security Management System
- D . Cyber Security Monitoring System
Which organization manages the ISA Secure conformance certification program?
Available Choices (select all choices that are correct)
- A . American Society for Industrial Security
- B . Automation Federation
- C . National Institute of Standards and Technology
- D . Security Compliance Institute
Latest ISA-IEC-62443 Dumps Valid Version with 88 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

