CrowdStrike CCFH-202 CrowdStrike Certified Falcon Hunter Online Training
CrowdStrike CCFH-202 Online Training
The questions for CCFH-202 were last updated at Feb 07,2026.
- Exam Code: CCFH-202
- Exam Name: CrowdStrike Certified Falcon Hunter
- Certification Provider: CrowdStrike
- Latest update: Feb 07,2026
Which of the following is a suspicious process behavior?
- A . PowerShell running an execution policy of RemoteSigned
- B . An Internet browser (eg, Internet Explorer) performing multiple DNS requests
- C . PowerShell launching a PowerShell script
- D . Non-network processes (eg, notepad exe) making an outbound network connection
Which field should you reference in order to find the system time of a *FileWritten event?
- A . ContextTimeStamp_decimal
- B . FileTimeStamp_decimal
- C . ProcessStartTime_decimal
- D . timestamp
What Search page would help a threat hunter differentiate testing, DevOPs, or general user activity from adversary behavior?
- A . Hash Search
- B . IP Search
- C . Domain Search
- D . User Search
An analyst has sorted all recent detections in the Falcon platform to identify the oldest in an effort to determine the possible first victim host What is this type of analysis called?
- A . Visualization of hosts
- B . Statistical analysis
- C . Temporal analysis
- D . Machine Learning
Refer to Exhibit.
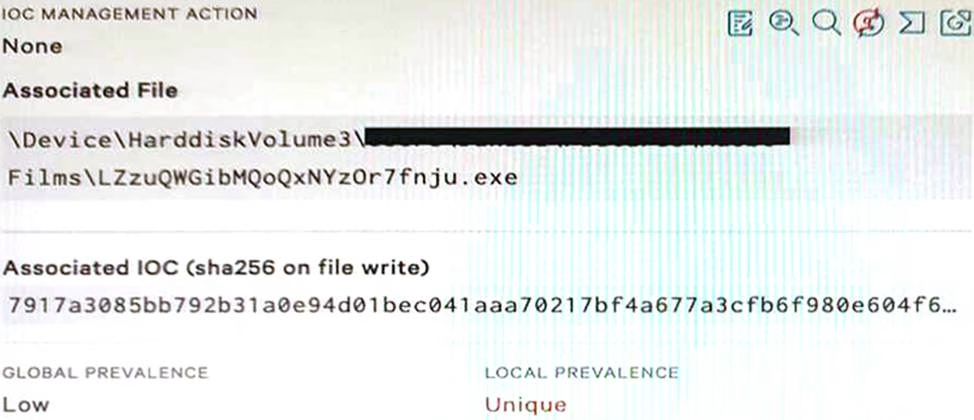
Falcon detected the above file attempting to execute.
At initial glance; what indicators can we use to provide an initial analysis of the file?
- A . VirusTotal, Hybrid Analysis, and Google pivot indicator lights enabled
- B . File name, path, Local and Global prevalence within the environment
- C . File path, hard disk volume number, and IOC Management action
- D . Local prevalence, IOC Management action, and Event Search
A benefit of using a threat hunting framework is that it:
- A . Automatically generates incident reports
- B . Eliminates false positives
- C . Provides high fidelity threat actor attribution
- D . Provides actionable, repeatable steps to conduct threat hunting
Which of the following is an example of a Falcon threat hunting lead?
- A . A routine threat hunt query showing process executions of single letter filename (e.g., a.exe) from temporary directories
- B . Security appliance logs showing potentially bad traffic to an unknown external IP address
- C . A help desk ticket for a user clicking on a link in an email causing their machine to become unresponsive and have high CPU usage
- D . An external report describing a unique 5 character file extension for ransomware encrypted files
The Falcon Detections page will attempt to decode Encoded PowerShell Command line parameters when which PowerShell Command line parameter is present?
- A . -Command
- B . -Hidden
- C . -e
- D . -nop
Which structured analytic technique contrasts different hypotheses to determine which is the best leading (prioritized) hypothesis?
- A . Model hunting framework
- B . Competitive analysis
- C . Analysis of competing hypotheses
- D . Key assumptions check
Which SPL (Splunk) field name can be used to automatically convert Unix times (Epoch) to UTC readable time within the Flacon Event Search?
- A . utc_time
- B . conv_time
- C . _time
- D . time
Latest CCFH-202 Dumps Valid Version with 60 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

