EC-Council 312-96 Certified Application Security Engineer (CASE) JAVA Online Training
EC-Council 312-96 Online Training
The questions for 312-96 were last updated at Feb 10,2026.
- Exam Code: 312-96
- Exam Name: Certified Application Security Engineer (CASE) JAVA
- Certification Provider: EC-Council
- Latest update: Feb 10,2026
Sam, an application security engineer working in INFRA INC., was conducting a secure code review on an application developed in Java. He found that the developer has used a piece of code as shown in the following screenshot.
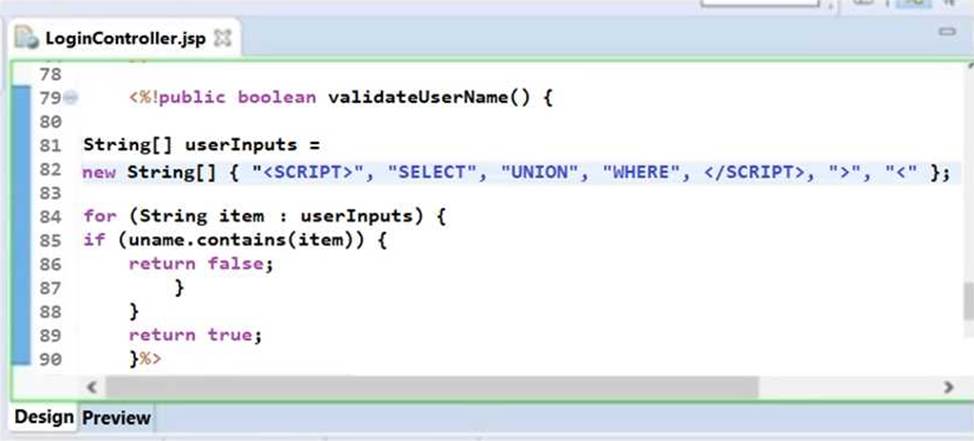
Identify the security mistakes that the developer has coded?
- A . He is attempting to use client-side validation
- B . He is attempting to use whitelist input validation approach
- C . He is attempting to use regular expression for validation
- D . He is attempting to use blacklist input validation approach
Identify the type of attack depicted in the following figure.
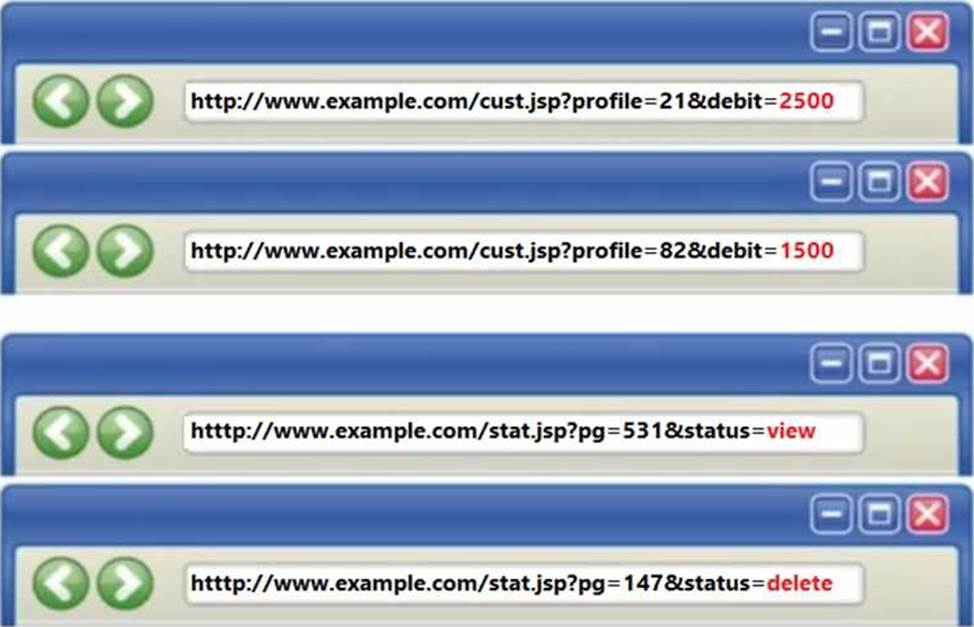
- A . SQL Injection Attacks
- B . Session Fixation Attack
- C . Parameter Tampering Attack
- D . Denial-of-Service Attack
According to secure logging practices, programmers should ensure that logging processes are not disrupted by:
- A . Catching incorrect exceptions
- B . Multiple catching of incorrect exceptions
- C . Re-throwing incorrect exceptions
- D . Throwing incorrect exceptions
Which of the threat classification model is used to classify threats during threat modeling process?
- A . RED
- B . STRIDE
- C . DREAD
- D . SMART
Which line of the following example of Java Code can make application vulnerable to a session attack?
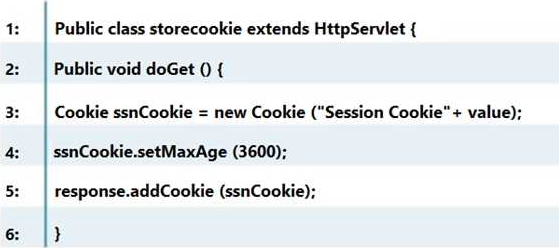
- A . Line No. 1
- B . Line No. 3
- C . Line No. 4
- D . Line No. 5
Alice, a Server Administrator (Tomcat), wants to ensure that Tomcat can be shut down only by the user who owns the Tomcat process. Select the appropriate setting of the CATALINA_HOME/conf in server.xml that will enable him to do so.
- A . < server port="" shutdown-"’ >
- B . < server port="-1" shutdown-*" >
- C . < server port="-1" shutdown="SHUTDOWN" >
- D . < server port="8080" shutdown="SHUTDOWN" >
Which of the following method will help you check if DEBUG level is enabled?
- A . isDebugEnabled()
- B . EnableDebug ()
- C . IsEnableDebug ()
- D . DebugEnabled()
Which of the following elements in web.xml file ensures that cookies will be transmitted over an encrypted channel?
- A . < connector lsSSLEnabled="Yes" / >
- B . < connector EnableSSL="true" / >
- C . < connector SSLEnabled="false" / >
- D . < connector SSLEnabled="true" / >
In which phase of secure development lifecycle the threat modeling is performed?
- A . Coding phase
- B . Testing phase
- C . Deployment phase
- D . Design phase
Identify the type of attack depicted in the figure below:
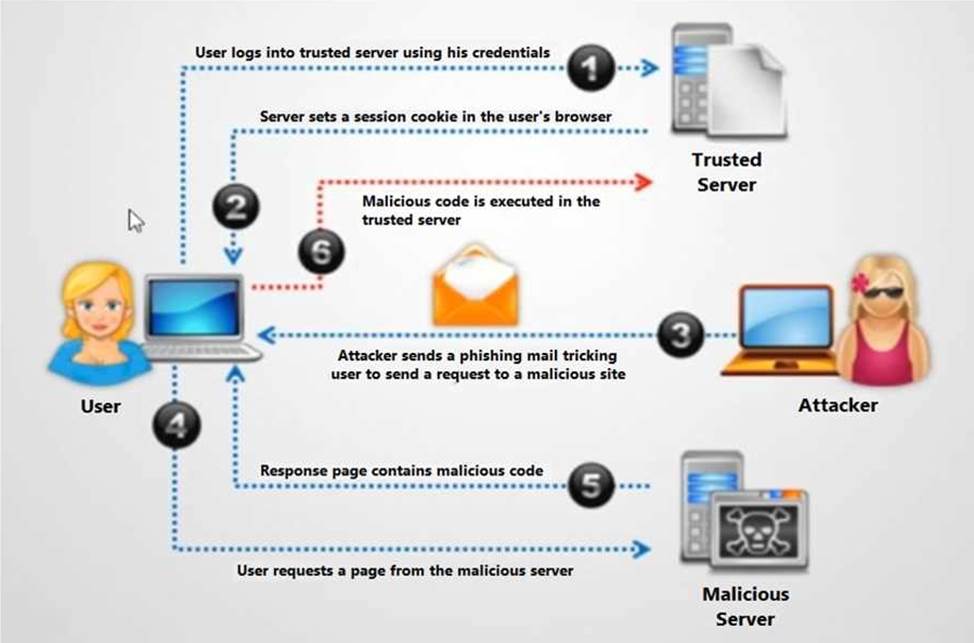
- A . XSS
- B . Cross-Site Request Forgery (CSRF) attack
- C . SQL injection attack
- D . Denial-of-Service attack
Latest 312-96 Dumps Valid Version with 47 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

