What could be the reason for this?
You are verifying the gossip encryption key currently used on your Consul cluster. You notice a
discrepancy between the encryption key identified in the configuration file vs. what is being reported by
the consul keyring command.
What could be the reason for this?
——————————————————————-
Excerpt from Configuration File:
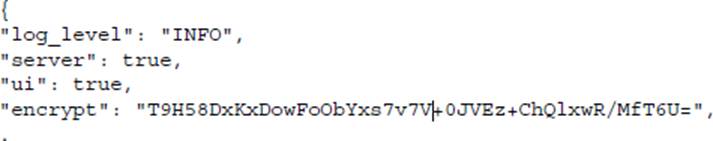
The output from consul keyring command:
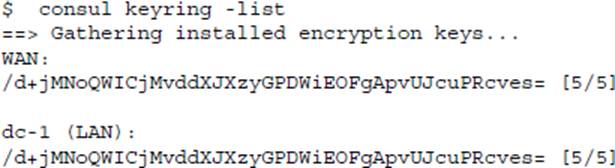
A . Consul automatically performs this key rotation for customers to satisfy the security/threat model
B. the encryption has been rotated with the consul keyring command
C. the key is automatically rotated by setting the -rotate flag in the Consul agent configuration
D. consul keyring is actually reporting the shared key used for clients, not servers
Answer: B
Explanation:
In short, the result of this observation was that the initial key used by Consul was set in the configuration file, but has since been rotated by a Consul admin. Once the new key was created, installed, and set as the primary, the old key was removed, leaving only the new encryption key being used cluster-wide. More information can be found here.
Latest Consul Associate Dumps Valid Version with 171 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

