Based on the policy, what change needs to be made to finish securing Consul?
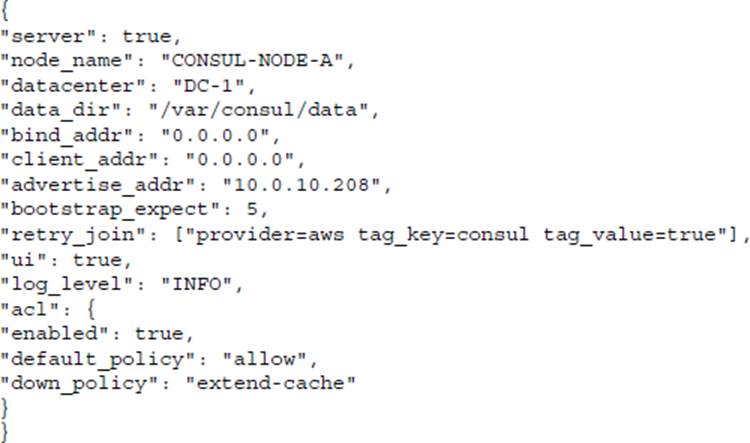
You have deployed a new Consul cluster to be used for service discovery between your microservices for a new application. In the configuration file, as shown below, you have enabled ACLs and bootstrapped the ACL system. However, clients are still being permitted to read and write to the ACL system or register services without a valid token.
Based on the policy, what change needs to be made to finish securing Consul?
A . reload the configuration on all the nodes after the bootstrap token was created
B. apply the bootstrap token to the other nodes
C. update the default_policy across all of the Consul nodes
D. configure the ACL policy for the anonymous token to deny all client requests
Answer: C
Explanation:
Once ACLs have been enabled and the bootstrap token has been created, you will need to modify the configuration file and change the default_policy to deny. This policy change will require all requests to Consul, including those from Consul servers, to have a valid token in order to communicate with the Consul service.
https://learn.hashicorp.com/consul/security-networking/production-acls
https://www.consul.io/docs/acl#acl-documentation
Latest Consul Associate Dumps Valid Version with 171 Q&As
Latest And Valid Q&A | Instant Download | Once Fail, Full Refund

